Trustifi to CheckPoint
Whenever Trustifi finds a new type of threat during an email scan, the information will be automatically sent to CheckPoint.
CheckPoint will then use this information to run a scan across all of the system’s protected endpoints to see if the threat may be located anywhere.
If a match is found, the system admins will receive an email alert containing information about which threat was found, on which devices, and more.
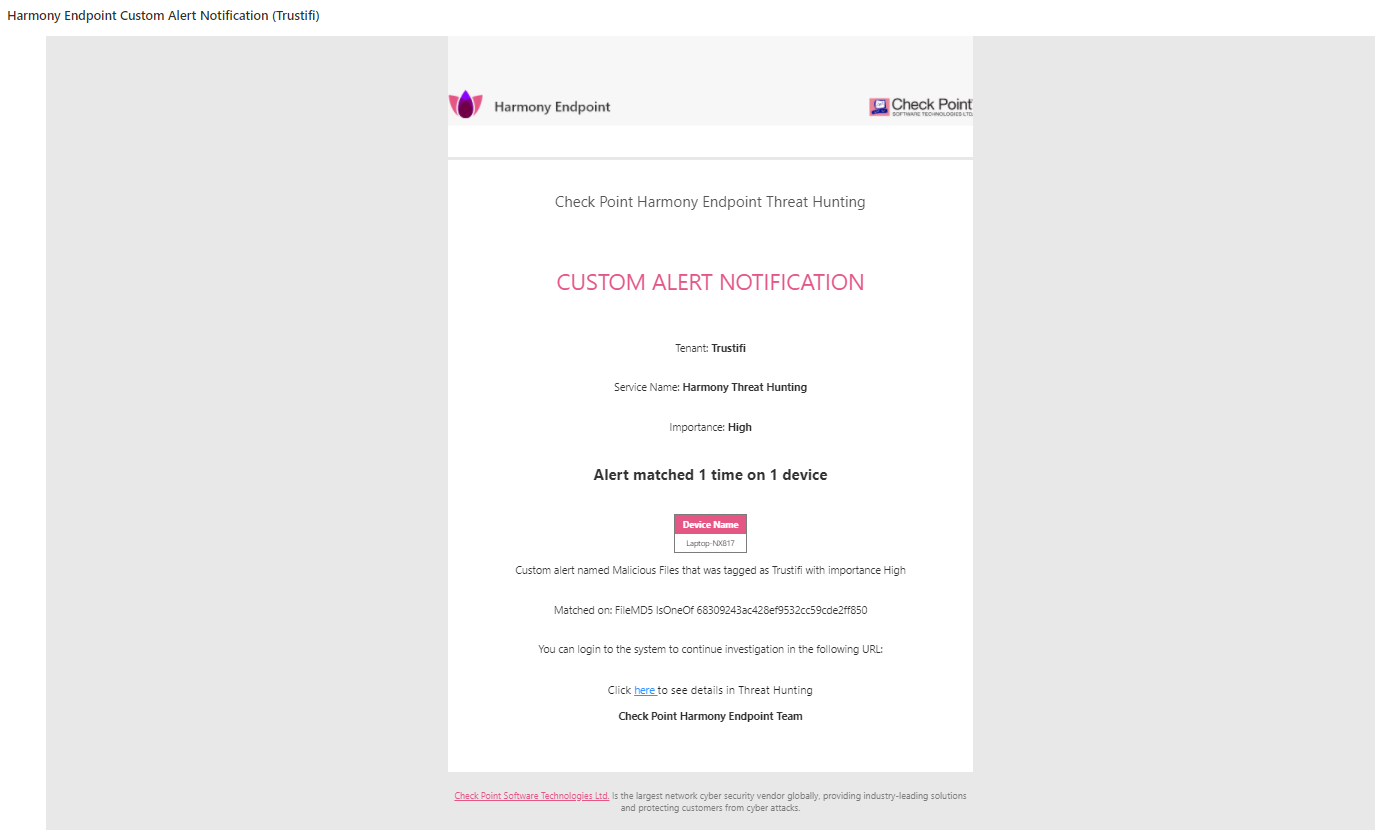
A threat notification from CheckPoint
CheckPoint to Trustifi
CheckPoint will continuously monitor the system’s protected endpoints.
If a new type of threat is found, CheckPoint will send the information to Trustifi. Trustifi will then use this threat intelligence to scan the system’s protected mailboxes and look for a match.
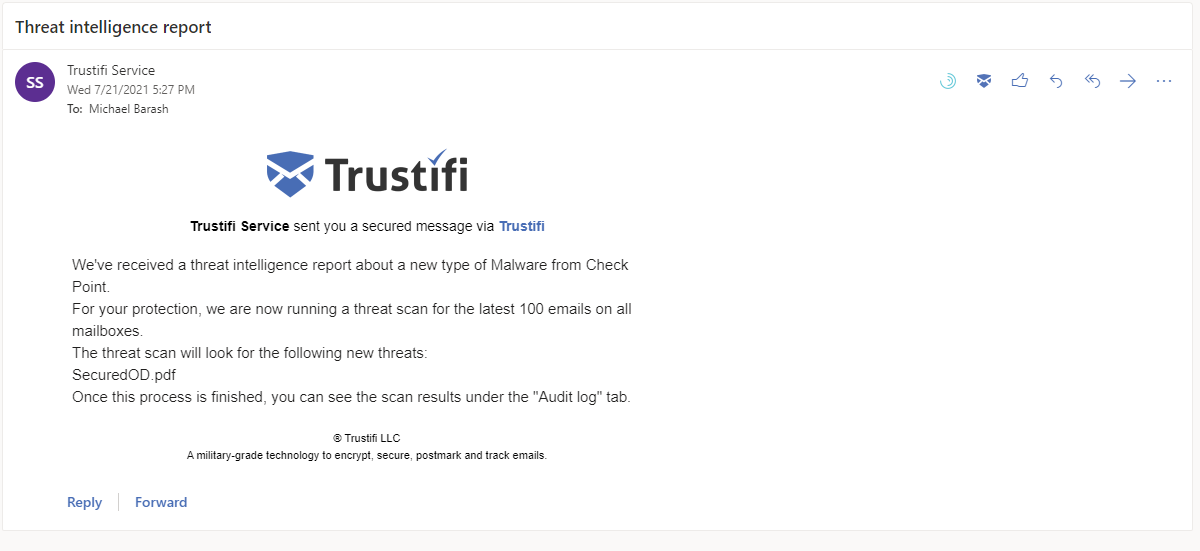
A threat intelligence notification from Trustifi.
Once the threat scan has been completed, the admin can view the scan results like so:
Log in to the Trustifi web portal and navigate to “Inbound Management”.
Open the “Threat Response” tab
Click on the “Actions” menu next to the scan log in the table
Click on the “Show Details” button
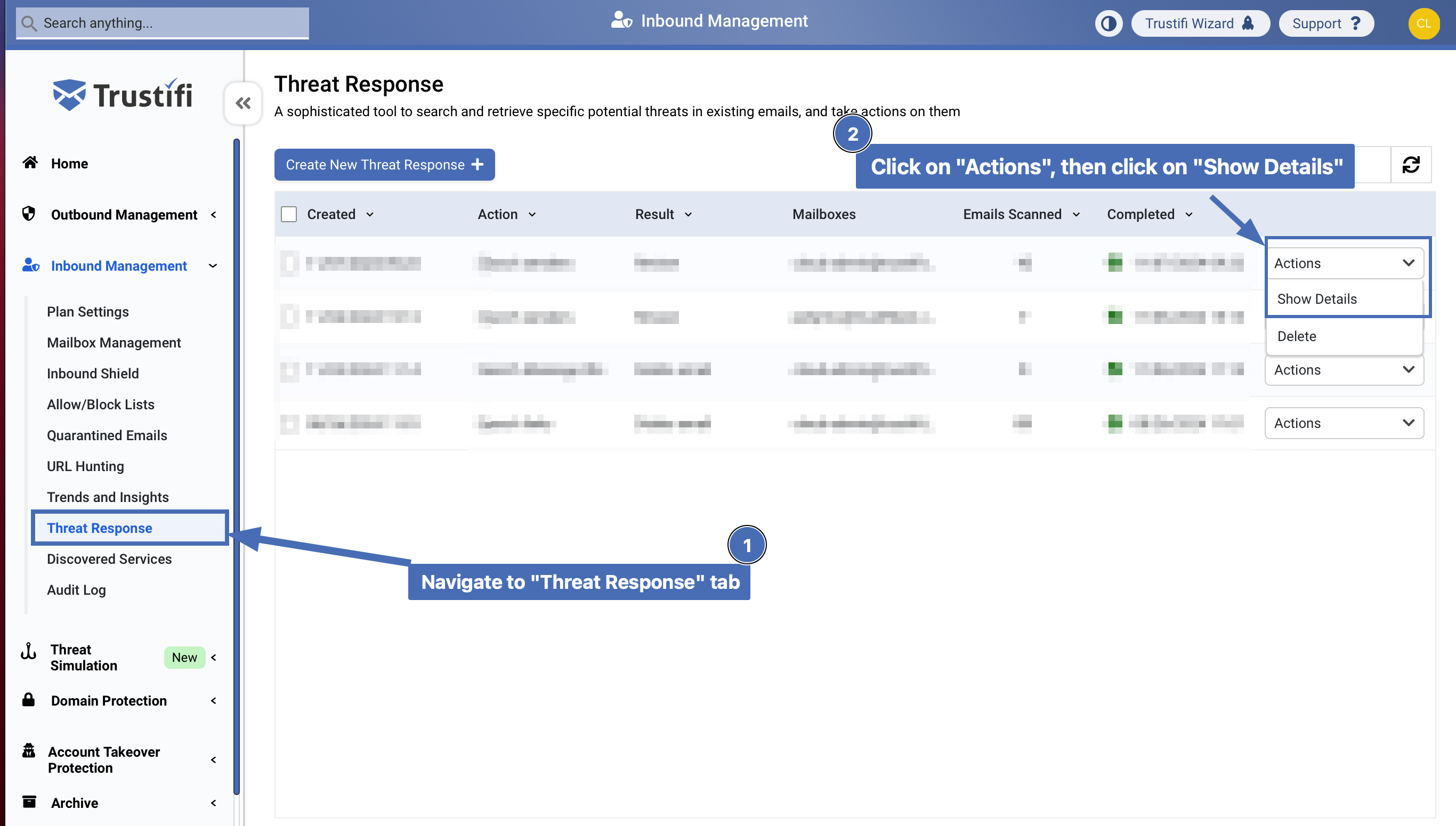
Finding the Threat Response log
When the “Show Details” is clicked, a new table will open with details regarding where the threat was found (if it was found), and relevant email details like the subject, mailbox, message ID, etc...
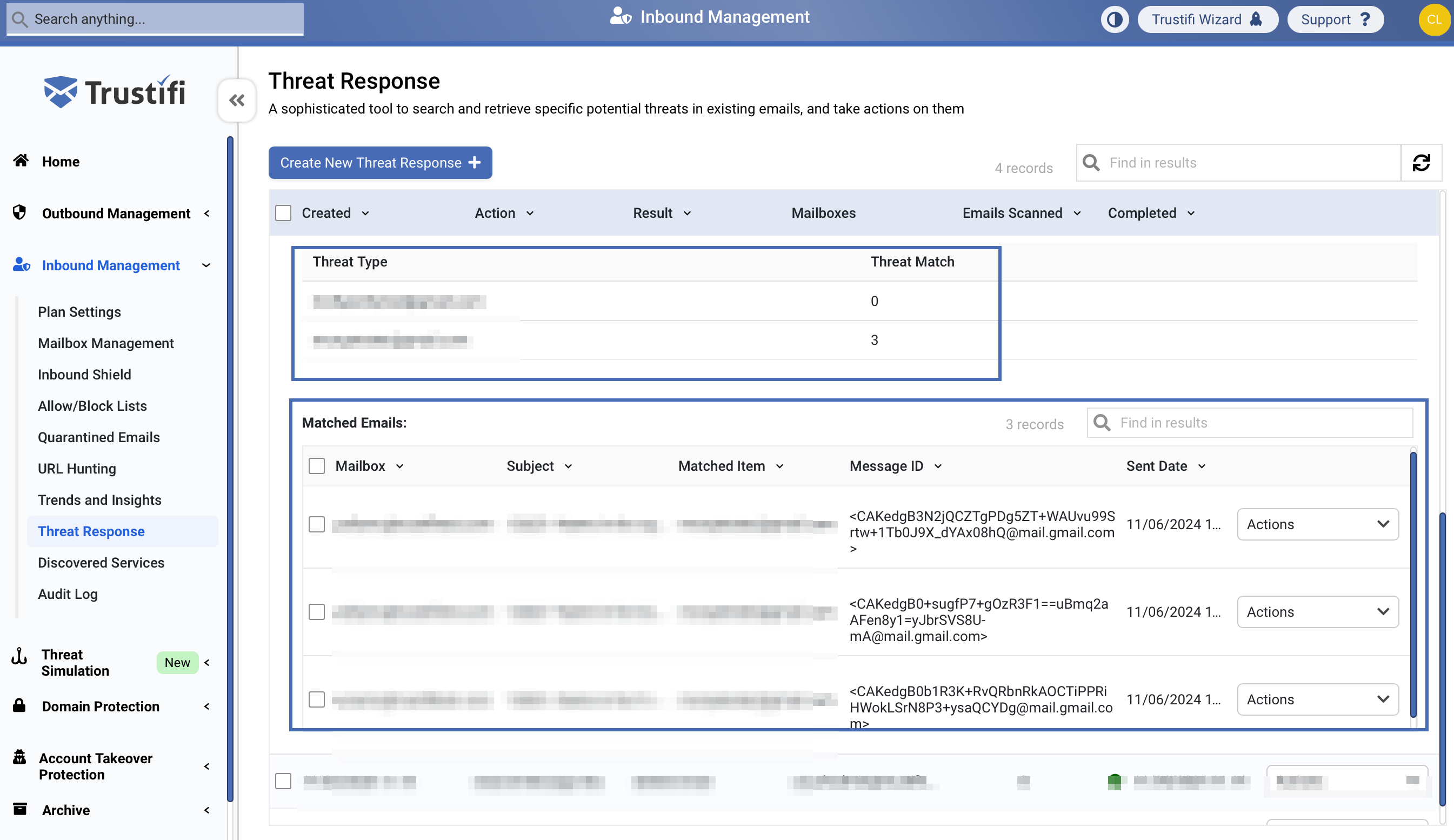
Viewing the Threat Response log.