Step 1 – Selecting mailboxes and choosing the “Threat Response” action
To start, you will need to navigate to the “Inbound Management” page and then to the “Threat Response” tab. Click on the “Create New Threat Response” button. You will now be presented with the Threat Response wizard window, which will guide you through the steps to complete the process. In the wizard select which mailboxes you wish to perform the process for (all/specific mailboxes). After you select the mailboxes click “Next”.
Step 2 – Selecting an action
In the next window, you will need to select an action (what you want to look for/scan). Click “Next” after you select an action.
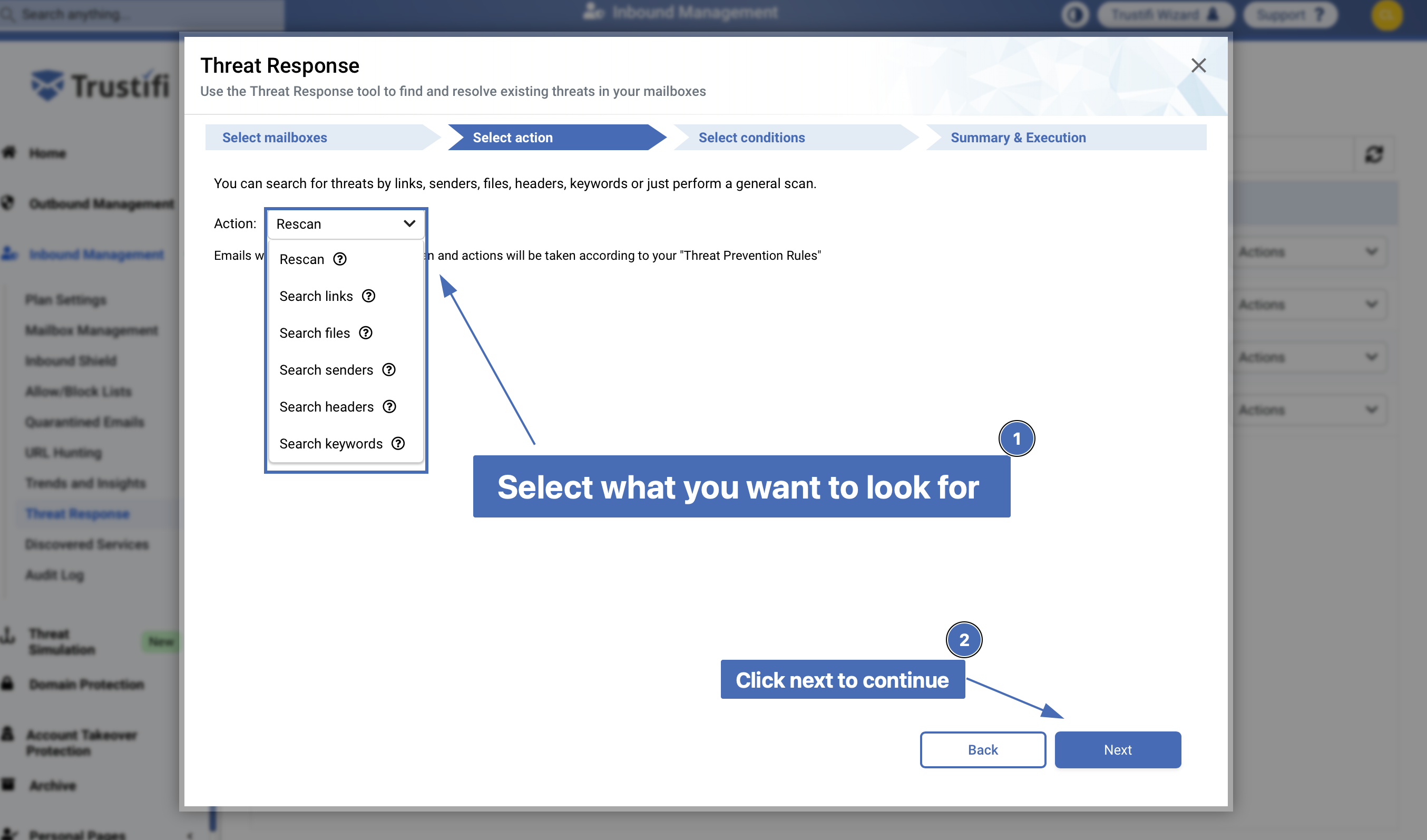
In the “Action” list you can choose from the following:
Rescan: performs a general scan to find all types of threats and spam. For this action you will not need to select a result, since the results are pre-determined by your existing threat prevention rules (which can be found under the “Threat Prevention” tab) and your block/allow lists (which can be found under the “Allow/Block lists” tab).
Search links: this will look for any specific URL(s) you provide. If found, the selected result will be applied to the email.
Search files: this will look for any specific file(s) you provide. If found, the selected result will be applied to the email.
Note: this action requires uploading the file itself. If you do not have the file and wish to search by file name only, please use “Search keywords”.
Search senders: this will look for emails sent from specific senders. If found, the selected result will be applied to the email.
Search headers: this will look for emails containing specific headers (key and value). If found, the selected result will be applied to the email.
Search keywords: this will look for emails containing specific keywords or phrases (in the body, subject, and in attachment names). If found, the selected result will be applied to the email
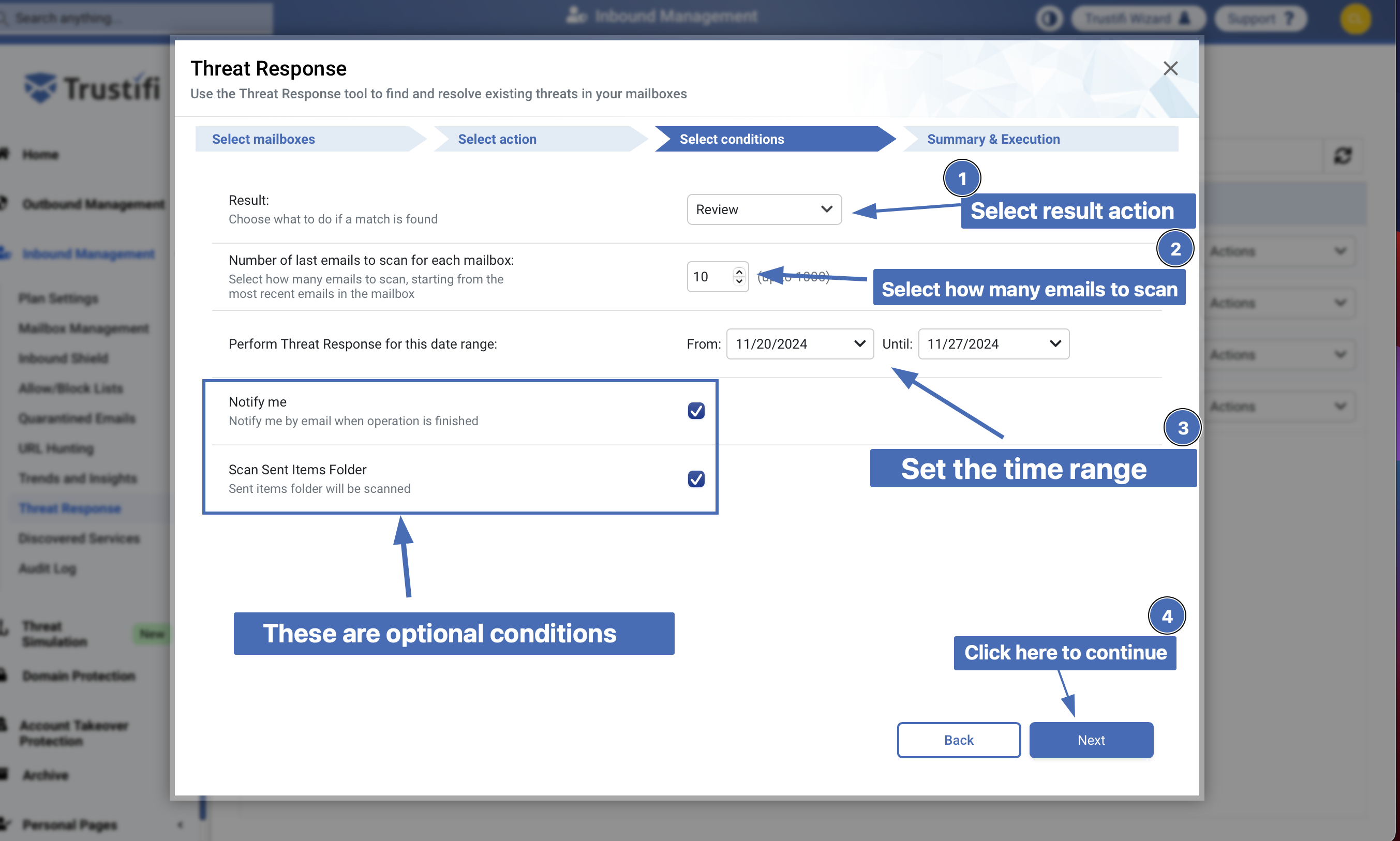
Step 3 – Select Conditions
In the next window, you will need to define the conditions and the result (what to do with emails that match your search).
Result actions:
Review - The email content will be displayed
Delete email - The email will be permanently deleted from the mailbox
Number of last emails to scan for each mailbox: Select how many emails to scan for each mailbox.
Note: In each mailbox, emails will be scanned chronologically from latest to oldest, and for each mailbox up to 1000 emails can be scanned.
Perform Threat Response for this date range: Define the time range of the search (from - until)
Optional conditions:
Notify me - When enabled, a notification email will be sent when the operation is finished.
Scan Sent Items Folder - Will also scan emails in the sent items folder.
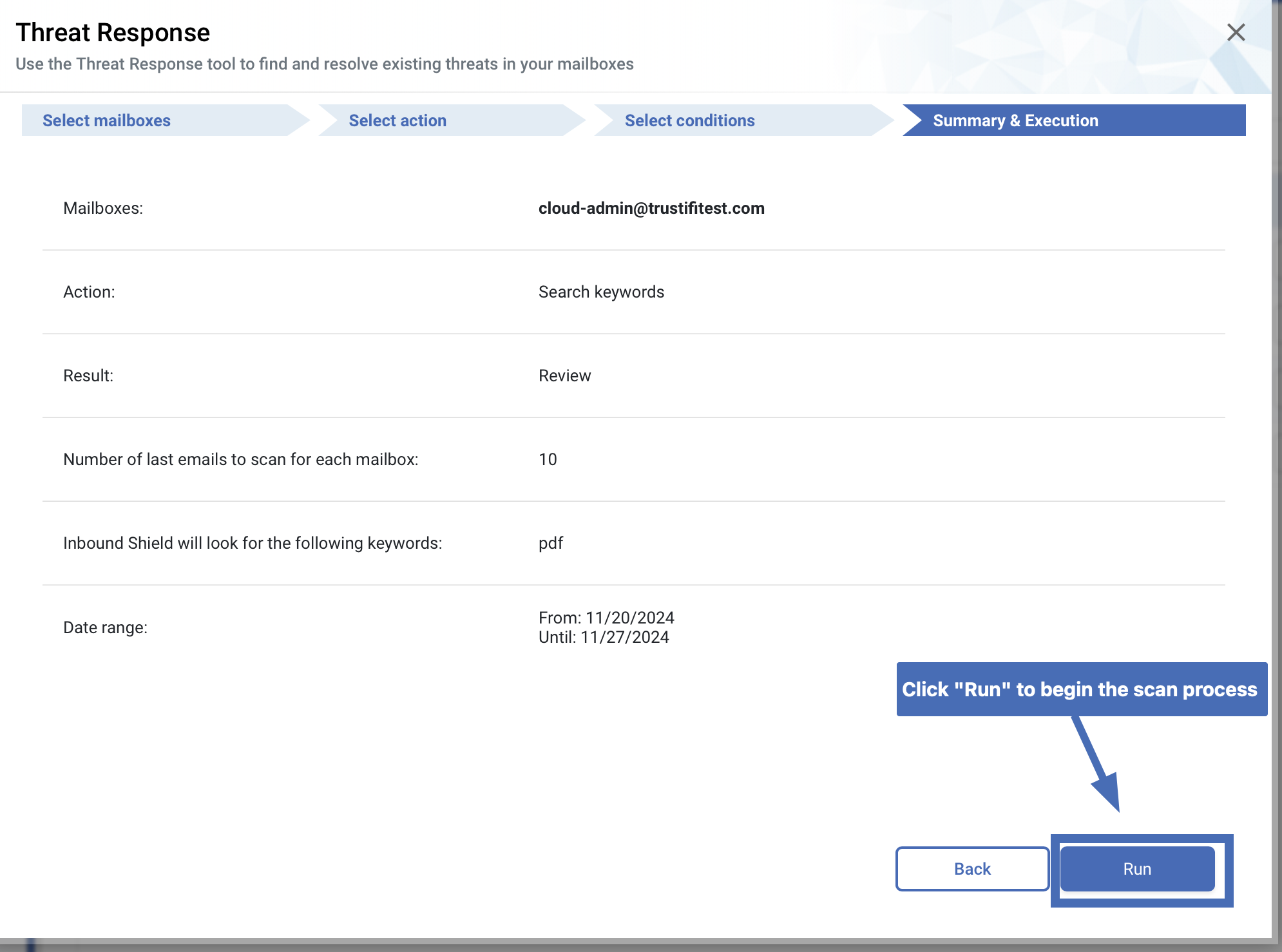
Step 4 – Summary & Execution
In this window, you will be presented with a summary of the process, so that you may review the details before the process begins. If you wish to change any of the previous configurations, simply click on the “Back” button.
This process can take some time, depends on your choices.
To begin the scan process, click on the “Run” button.
Step 5 – Viewing results
Once the process is finished, you can view the results in the “Threat Response” tab.
Click on the “Actions” menu next to the “Threat Response” you’ve created.
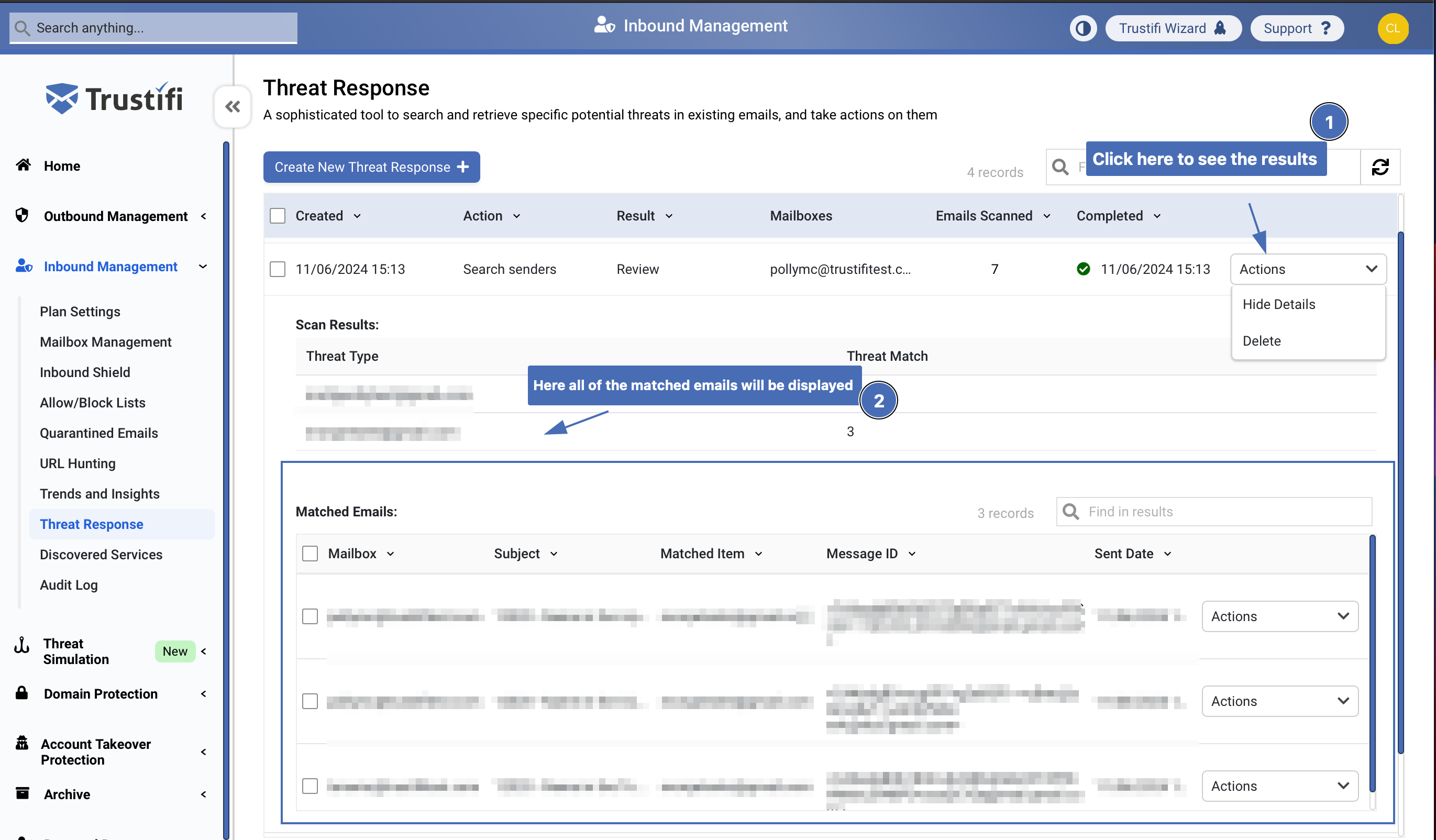
When you click on the “Show Details” button, a new table will open which will show you a detailed list of:
Which mailboxes the Threat Response process was performed on
The subject of the emails that match the search criteria
The matched item that was found in those emails
The message ID for each matched email
The date that those emails were sent