Note: This configuration guide utilizes the "Partner organization" connector type and is suitable for both older and newer O365 tenants. If your Microsoft/O365 tenant is older than Jan 1, 2023 and you need to use the "Your organization" connector type, please refer to our guide for older O365 tenants.
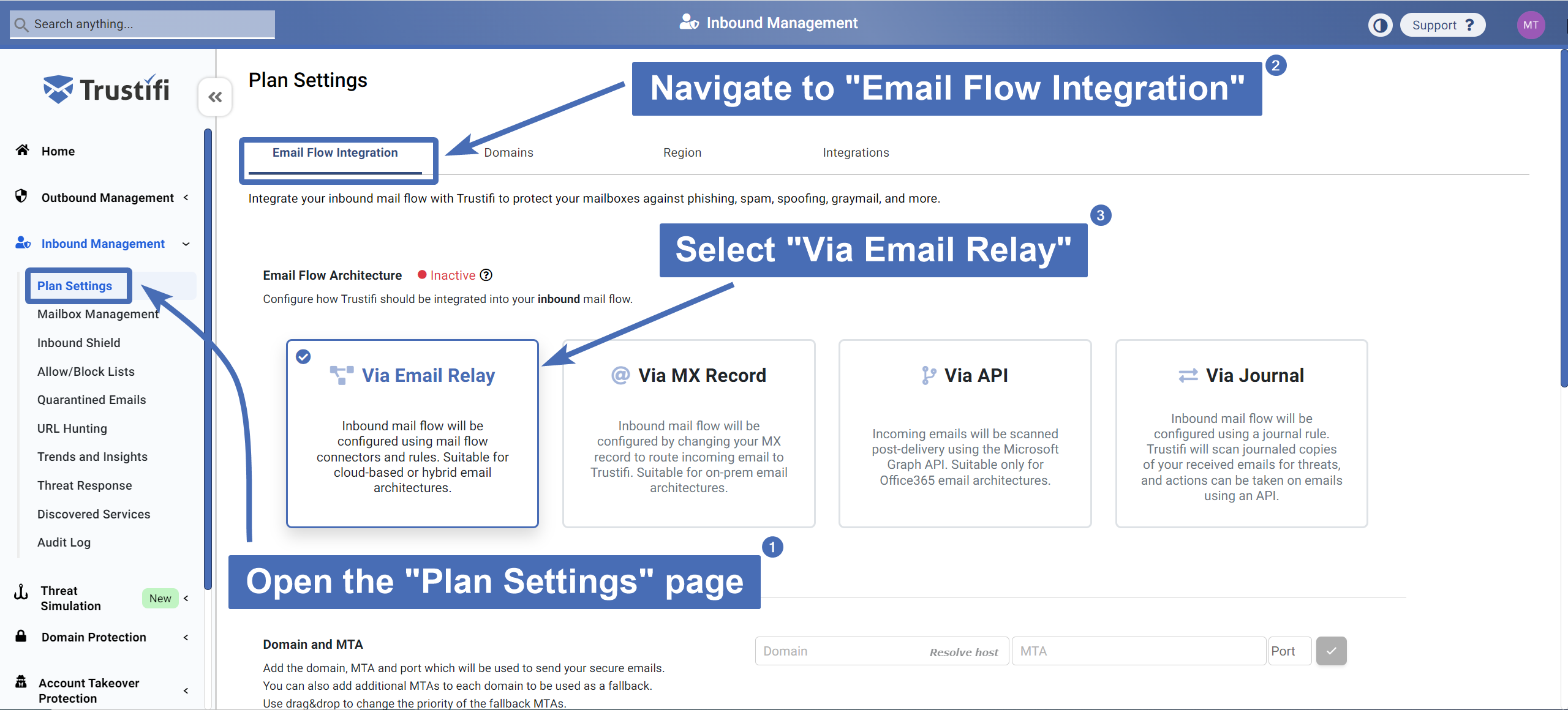
Step 1 – Navigating to “Email Relay Integration”
First, you will need to log into the Trustifi web portal using your admin credentials.
Once logged in, click on “Inbound Management” on the left side navigation bar and then click on the “Plan Settings” page. Make sure the selected architecture is "via Email Relay".
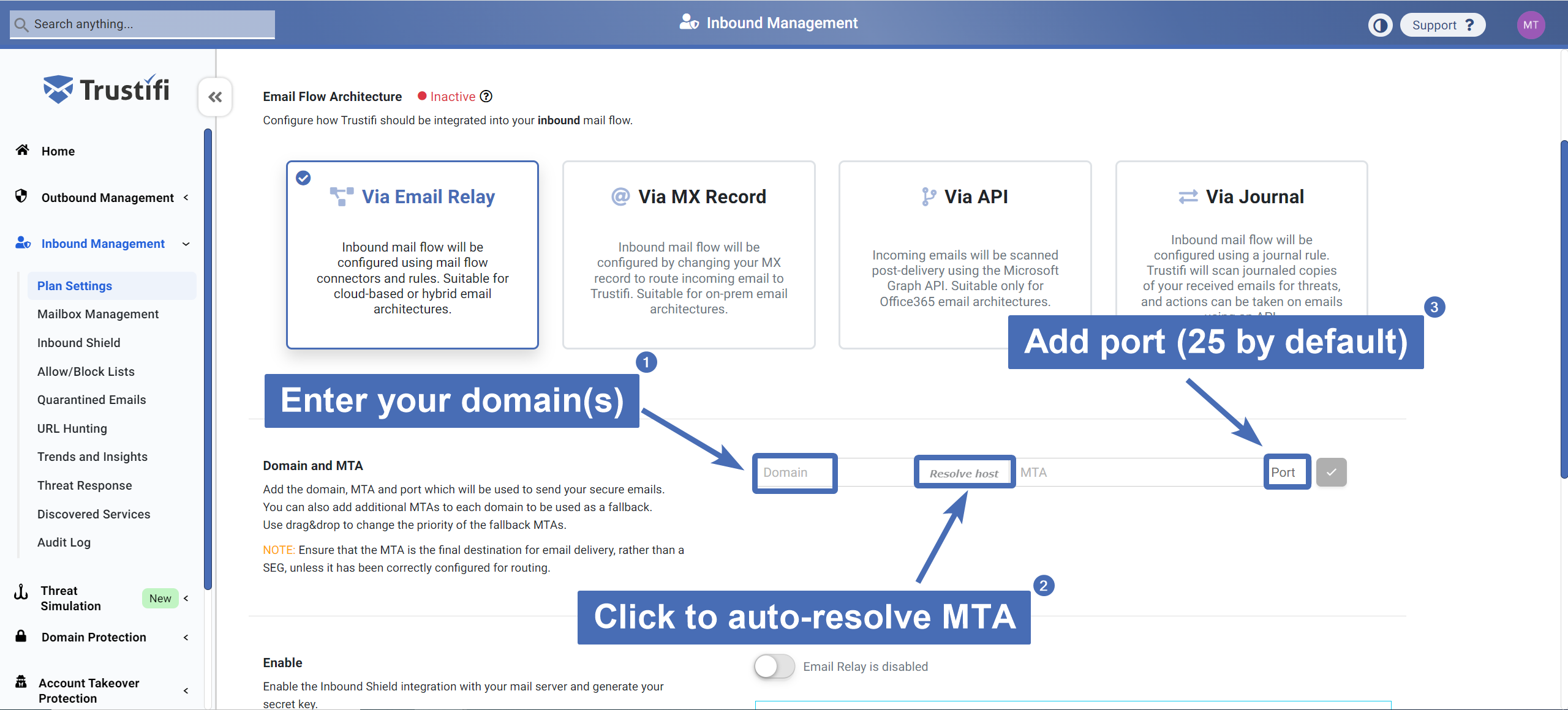
Step 2 – Adding your domain, MTA, and port
Under the “Domain and MTA” section you will need to enter your domain, Mail Transfer Agent (MTA) and port.
If you are not sure what your MTA is, you can click “resolve host” to auto-fill the “MTA” field.
The port number will usually be 25.
Notes:
If you have several domains which should be protected you can add multiple domains with their corresponding MTAs. For each domain, up to 3 MTAs can be added - the first MTA will be used by default and the other 2 will be used as a fallback in case the first MTA fails.
If you are planning to use Trustifi’s inbound relay alongside an existing SEG (secure email gateway), do not use the “Resolve host” function as it will lead to a mail loop. Instead, manually add your email server’s MTA.
Step 3 – Enabling the Inbound Email Relay
After your domain, MTA, and port have been added, simply click the “Enable” toggle and confirm in the pop-up window
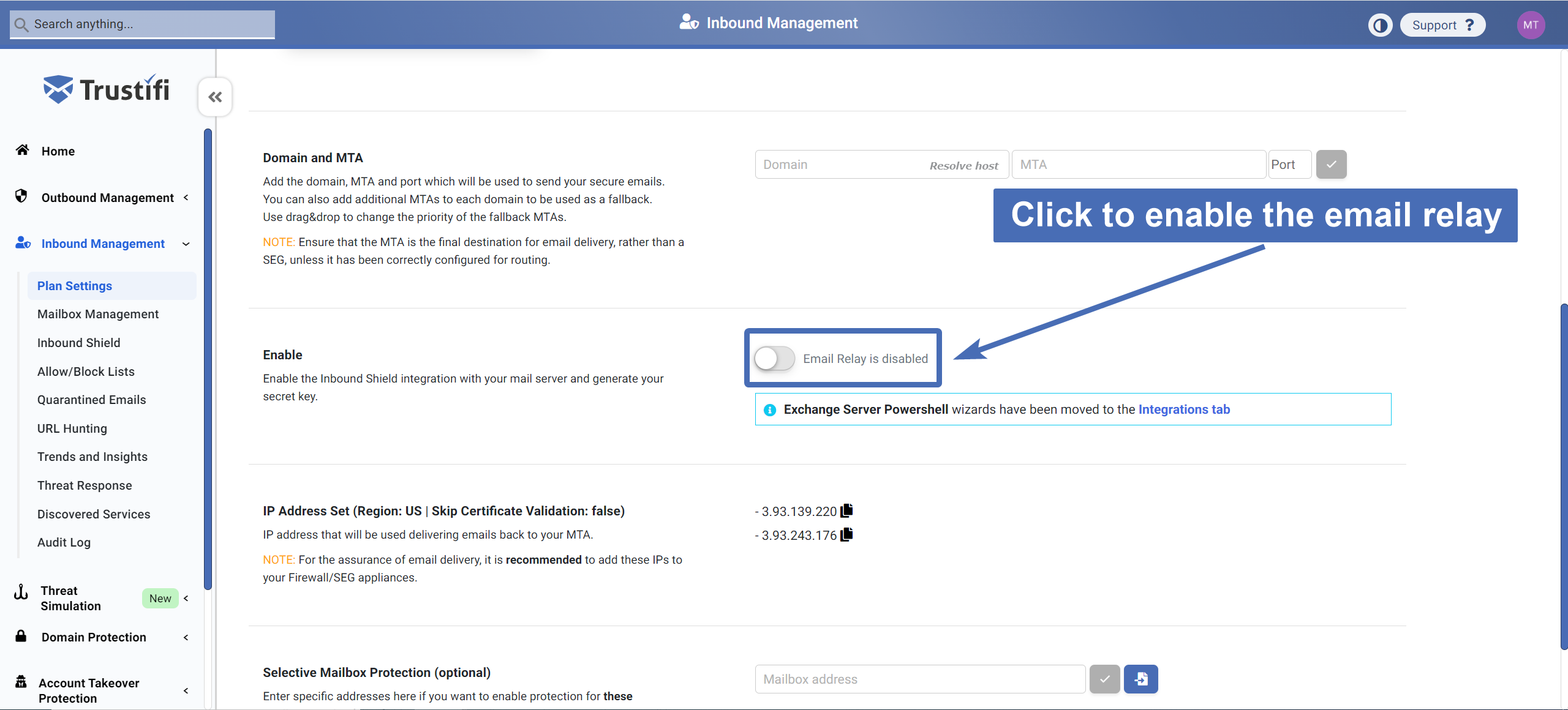
After the Inbound Email Relay has been enabled, your Email Relay key will be generated. You can copy this key now to use it later in configuration.
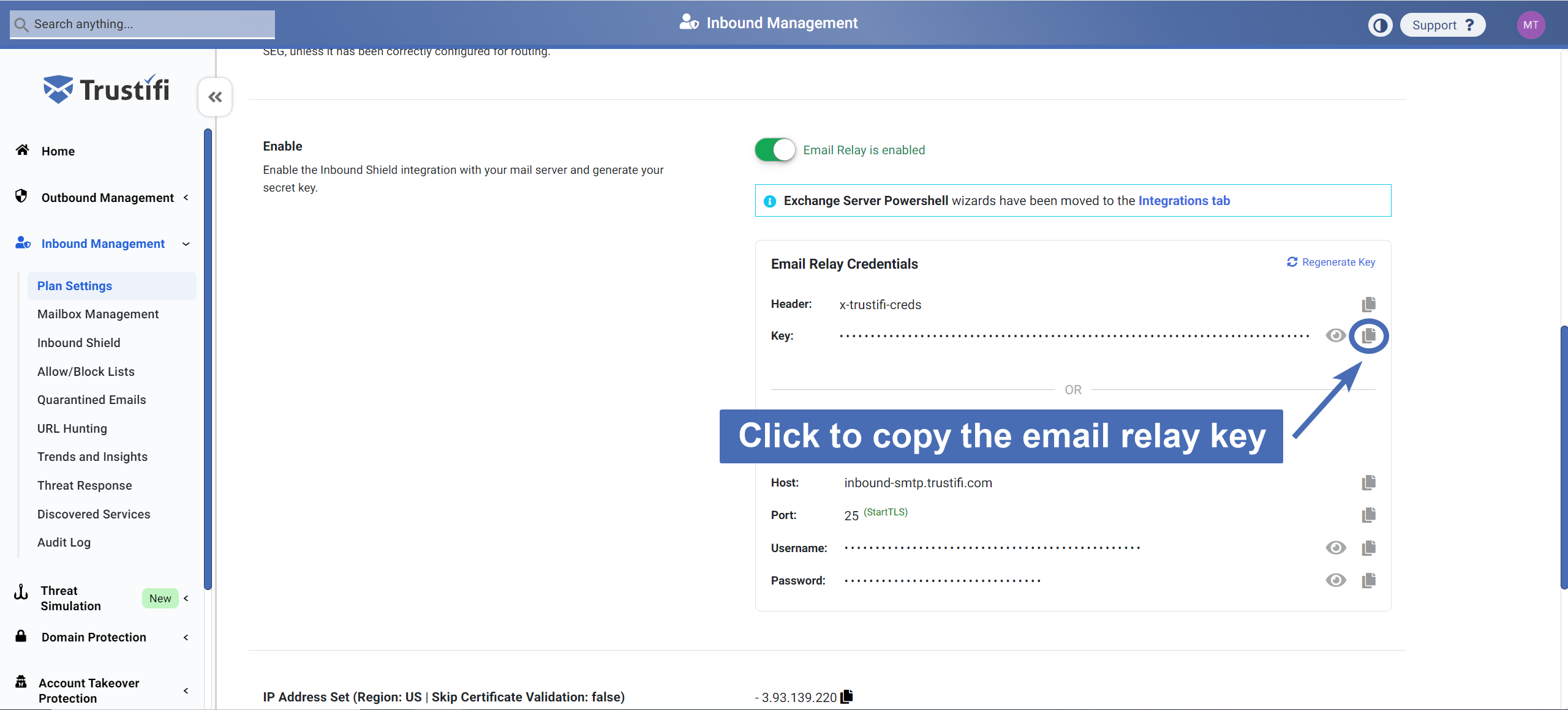
Note: This action will not yet change anything in your server’s inbound mail flow. Mail traffic will only be routed through Trustifi after the mail-flow rule and connectors have been set up.
Step 4 – Navigating to the Exchange Admin Center – Mail flow connectors
Navigate and log into the “Exchange admin center” using your admin credentials.
After you have logged in, navigate to the “Mail flow” – “Connectors” page.
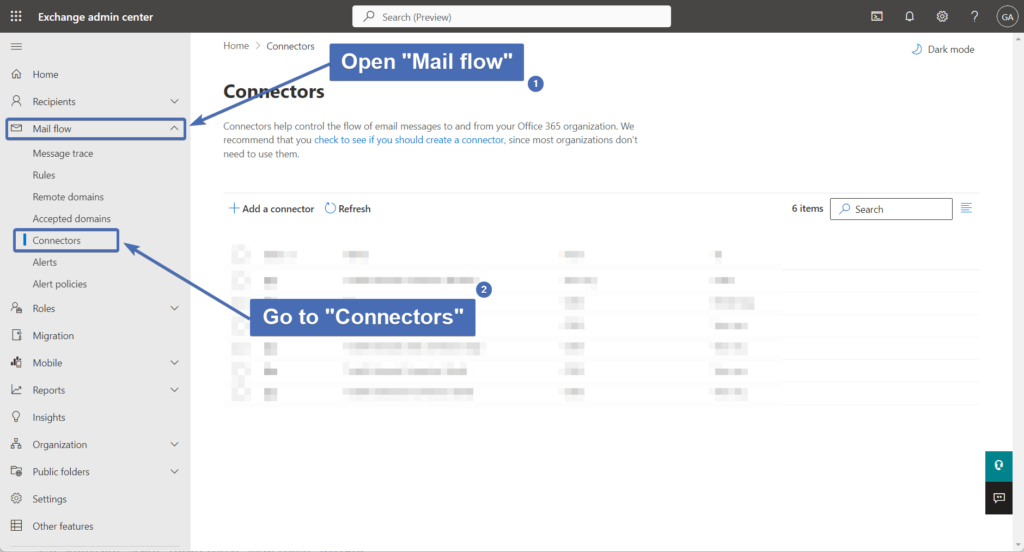
Step 5 – Creating the “receive” connector
Click on the “Add a new connector” button to open the “New connector” interface.

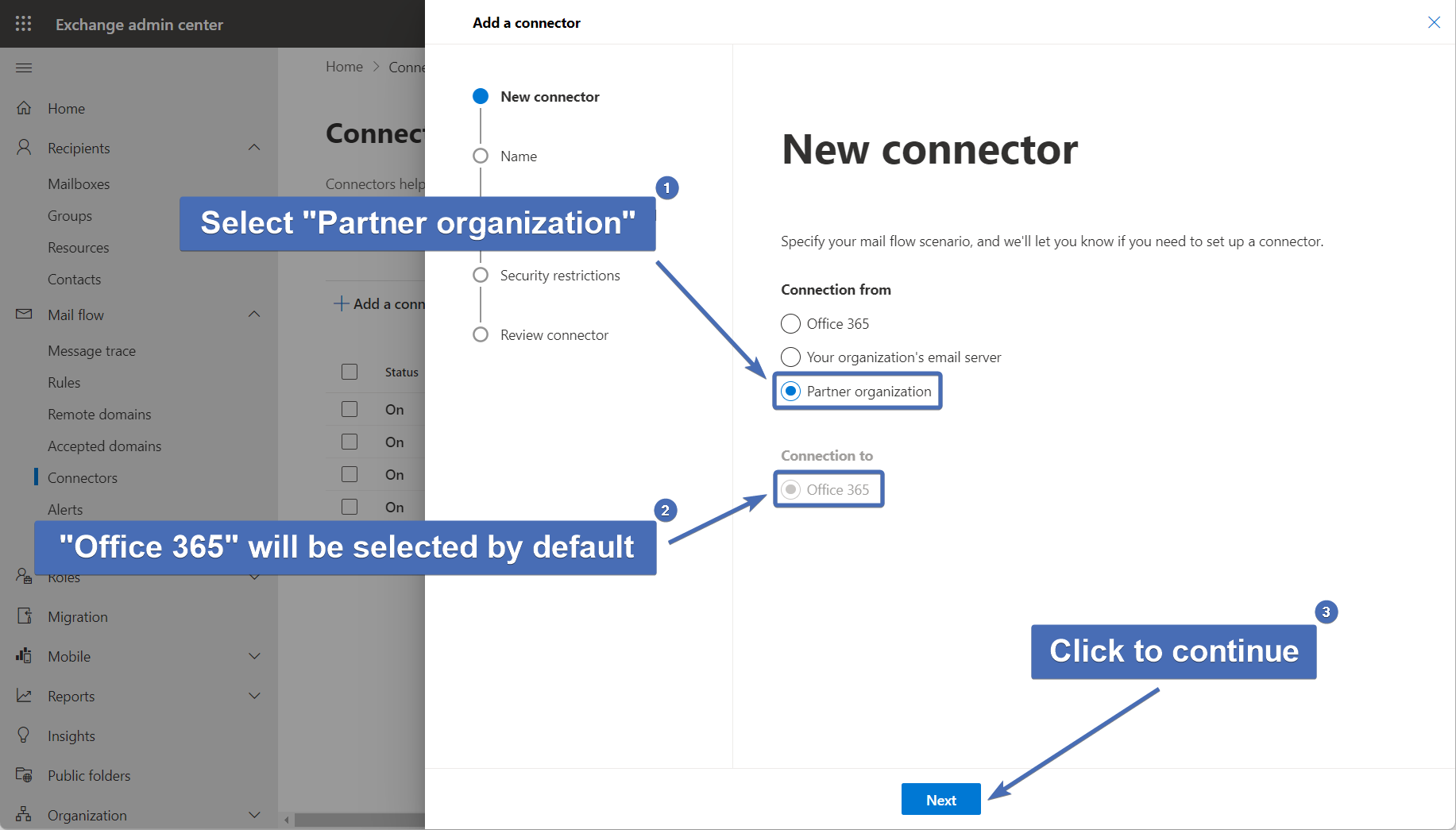
Step 6 – Selecting a mail flow scenario
Under “Connection from” select “Partner organization” and under “Connection to” select the default option “Office 365”.
Continue by clicking on "Next".
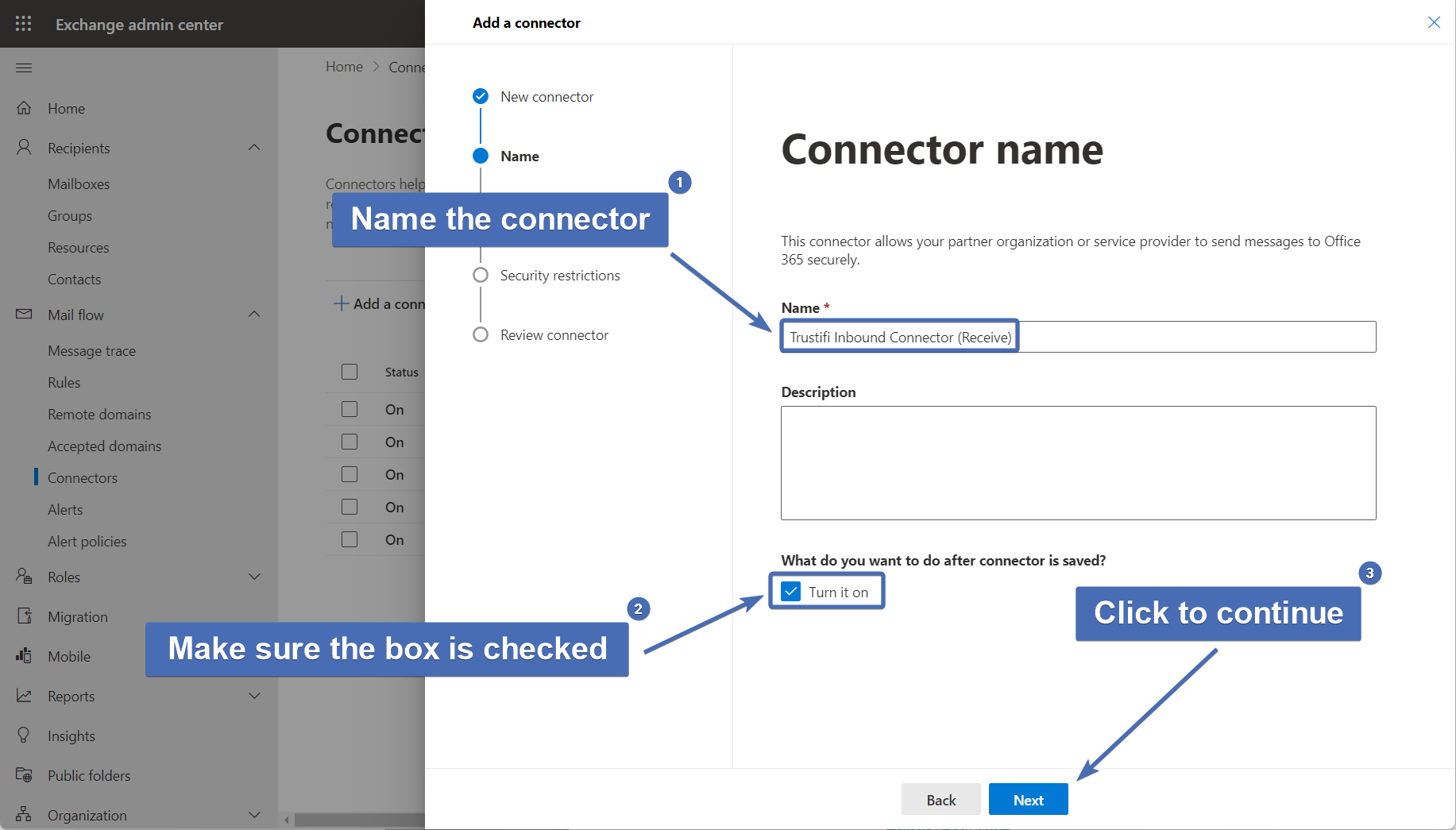
Step 7 – Naming and describing the connector
In the “Name” field enter the following name – “Trustifi Inbound Connector (Receive)".
In the "Description" field you can add any description you like (optional). Make sure the "Turn it on" box is checked. You can continue by clicking on "Next".
Step 8 – Authenticating sent email
Here you need to select “By verifying that the IP address of the sending server matches one of these IP addresses that belong to your organization”.
Add the following IPs and click on the "+" button to add each one:
3.93.243.176
3.93.139.220
3.251.32.127
54.195.145.1
52.89.220.23
52.37.228.167
52.54.159.237
52.73.143.252
3.221.25.19
34.192.117.166
44.209.231.3
35.172.145.174
After all IPs have been added, click on "Next" to continue.
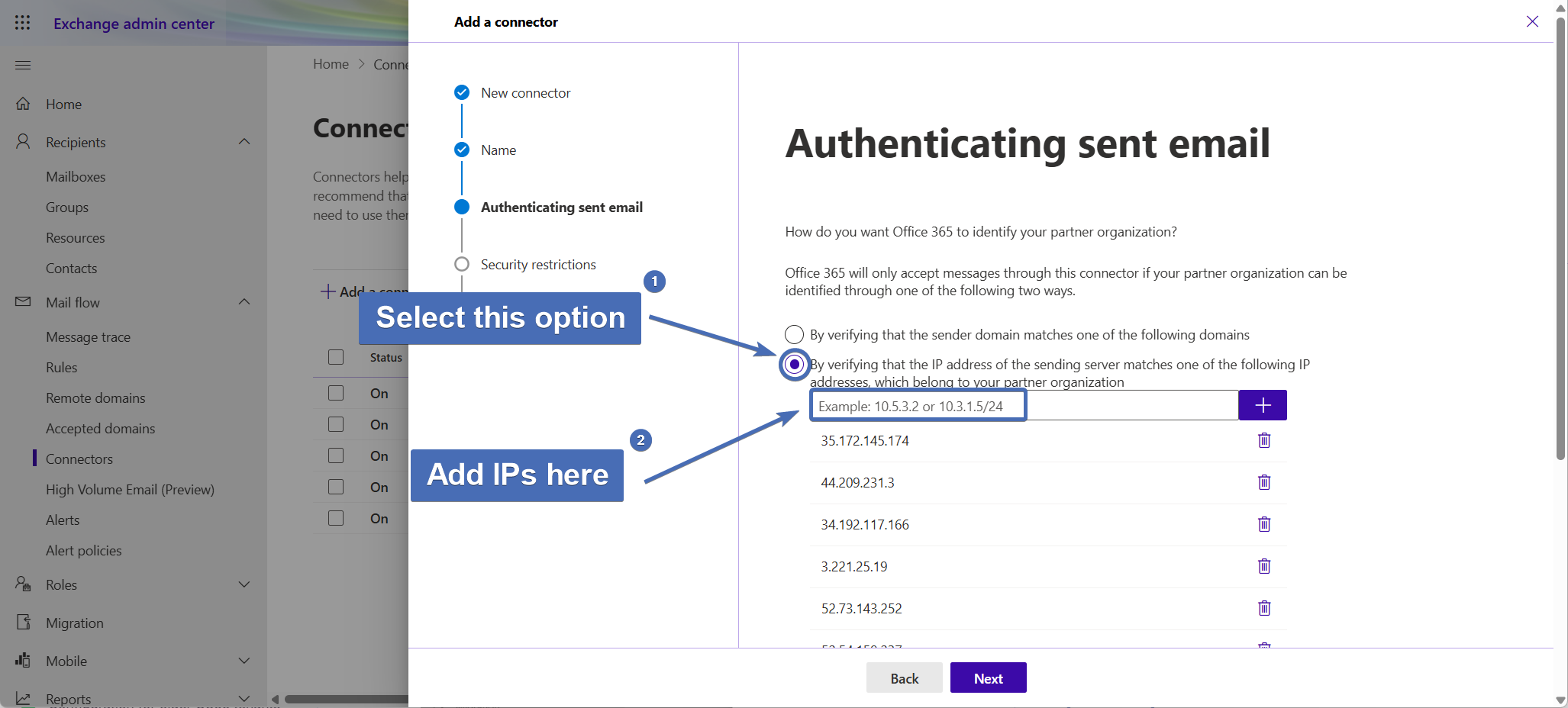
Step 9 – Security restrictions
Make sure the "Reject email messages if they aren't sent over TLS" box is checked, then click "Next" to continue.
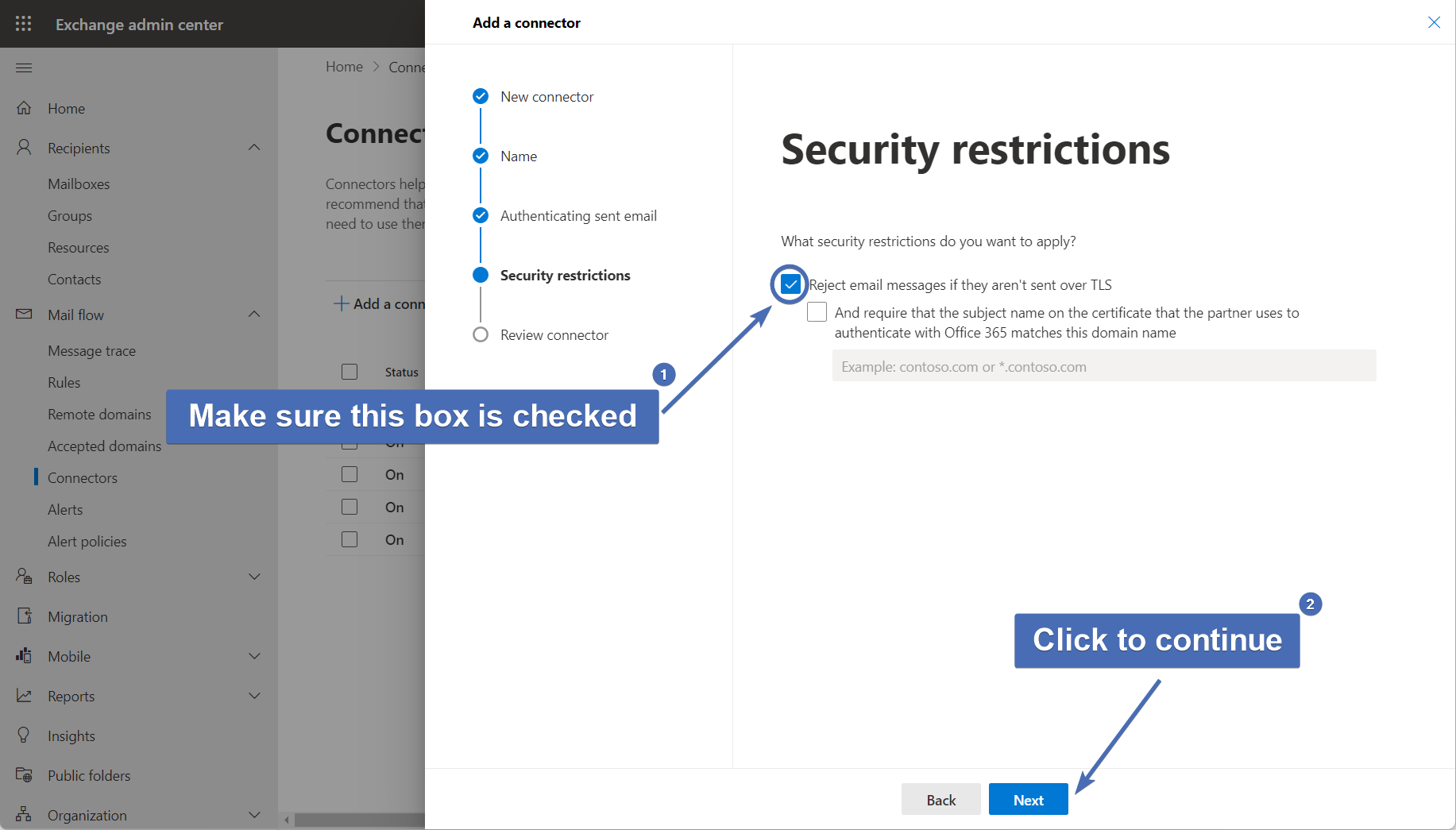
Step 10 – Reviewing the connector
Confirm that all settings are correct and finish by clicking on “Create connector”.
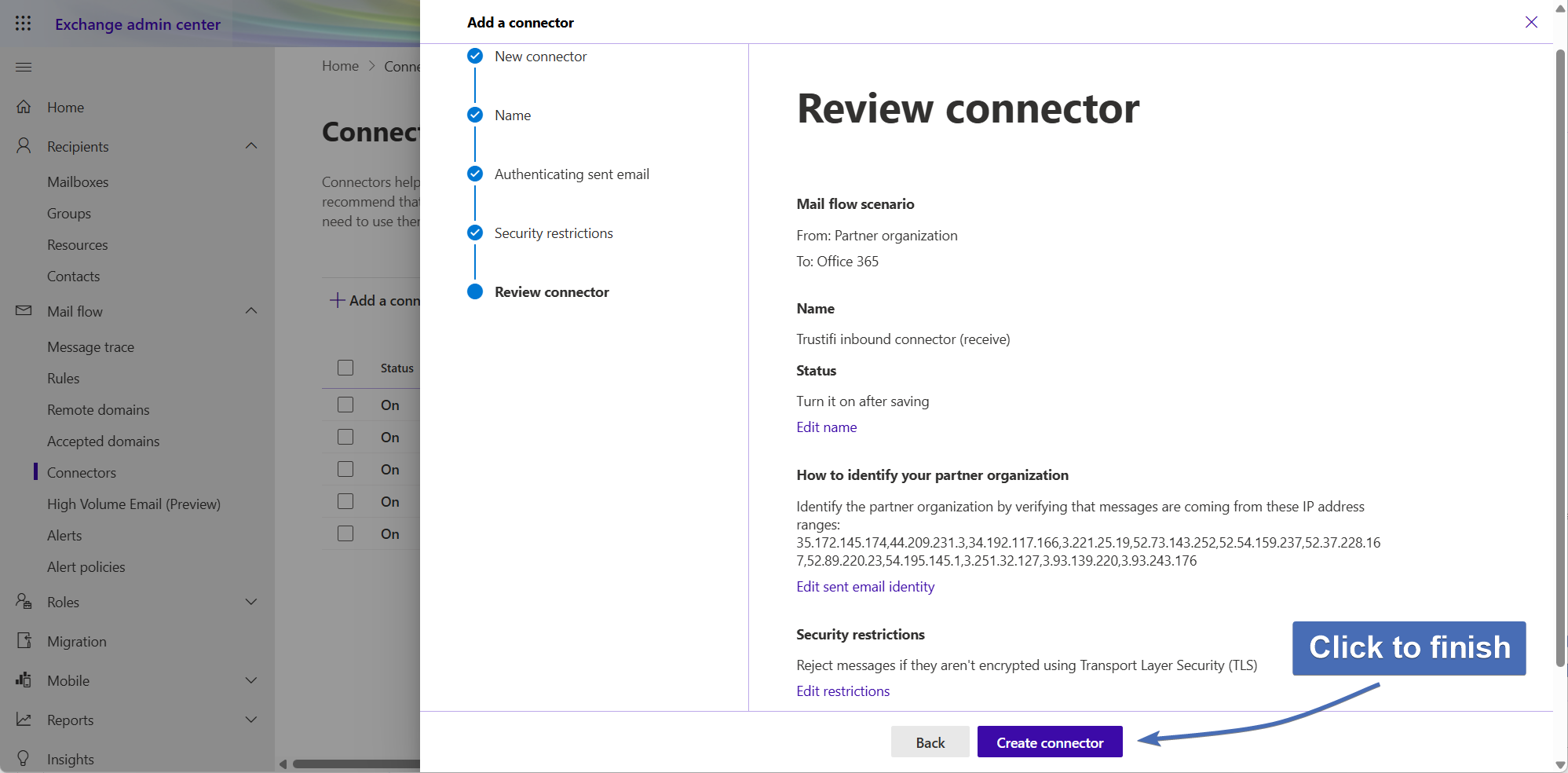
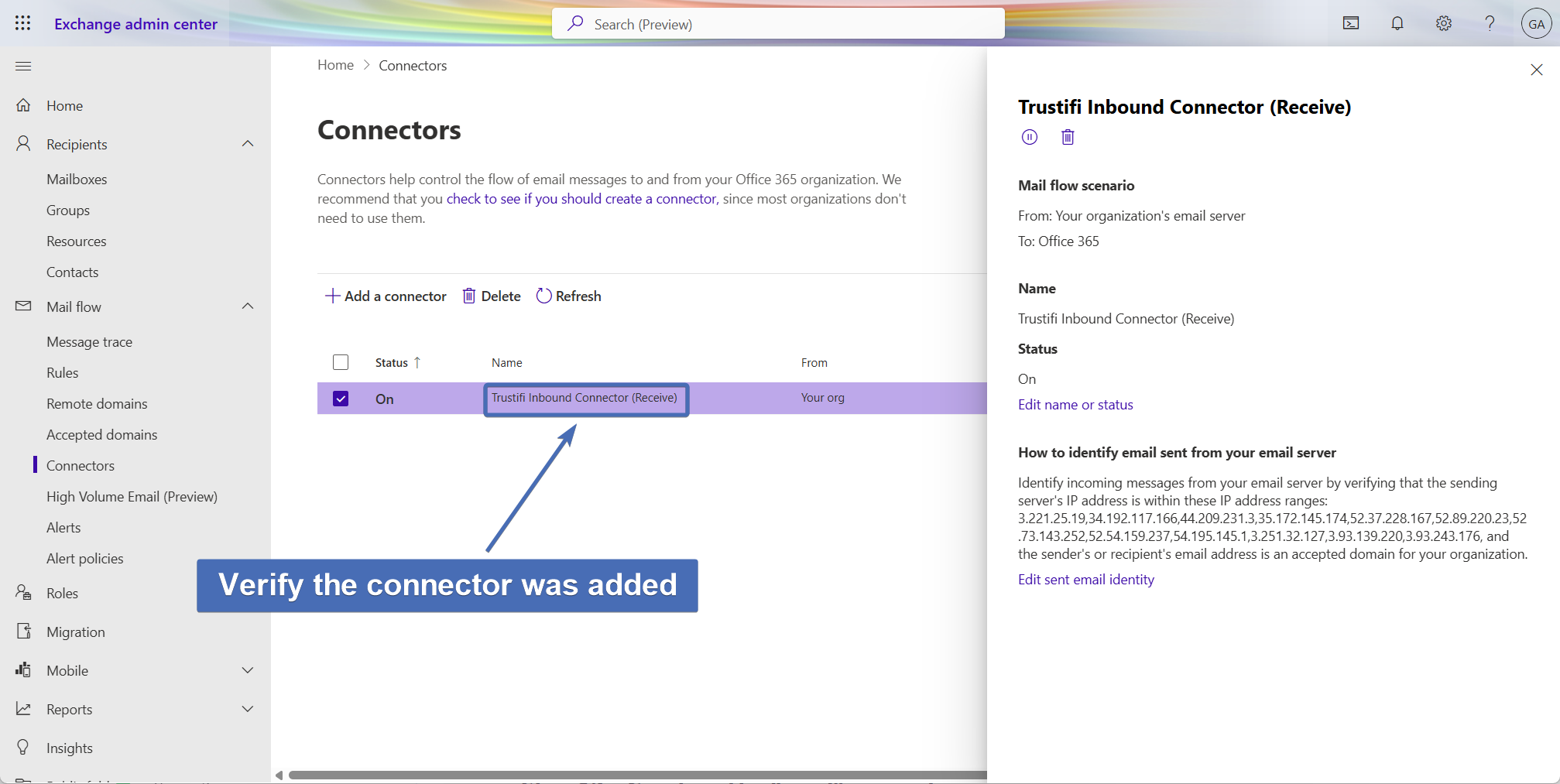
Step 11 – Confirming the connector has been added
Confirm the “Trustifi Inbound Connector (Receive)" connector has been added to the connector list.
Step 12 – Creating the “send” connector
Click on the "Add a connector" button to create a new connector.
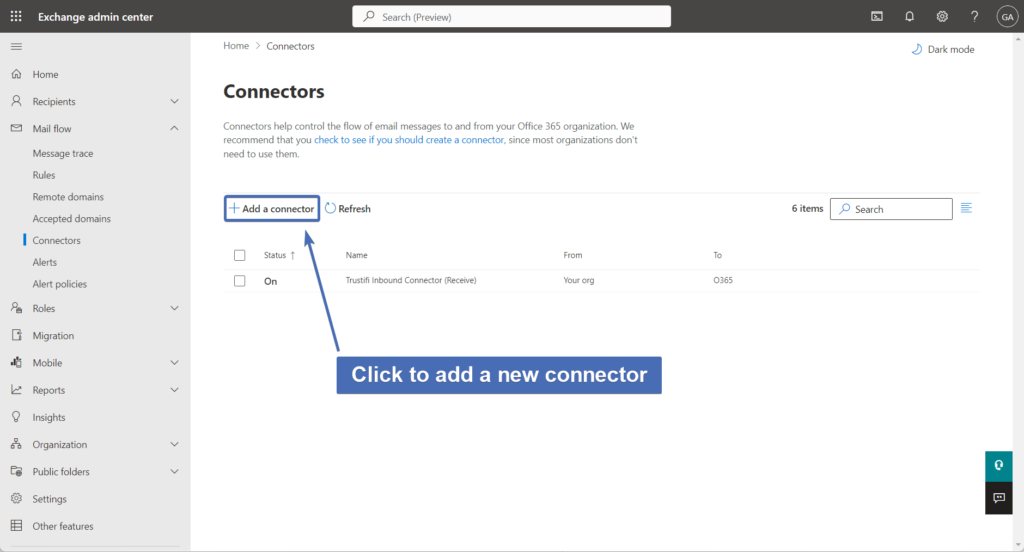
Step 13 – Selecting a mail flow scenario
Here, you will need to select the mail flow scenario.
Under “Connection from” select “Office 365”, and under “Connection to” select “Partner organization” and continue by clicking “Next”.
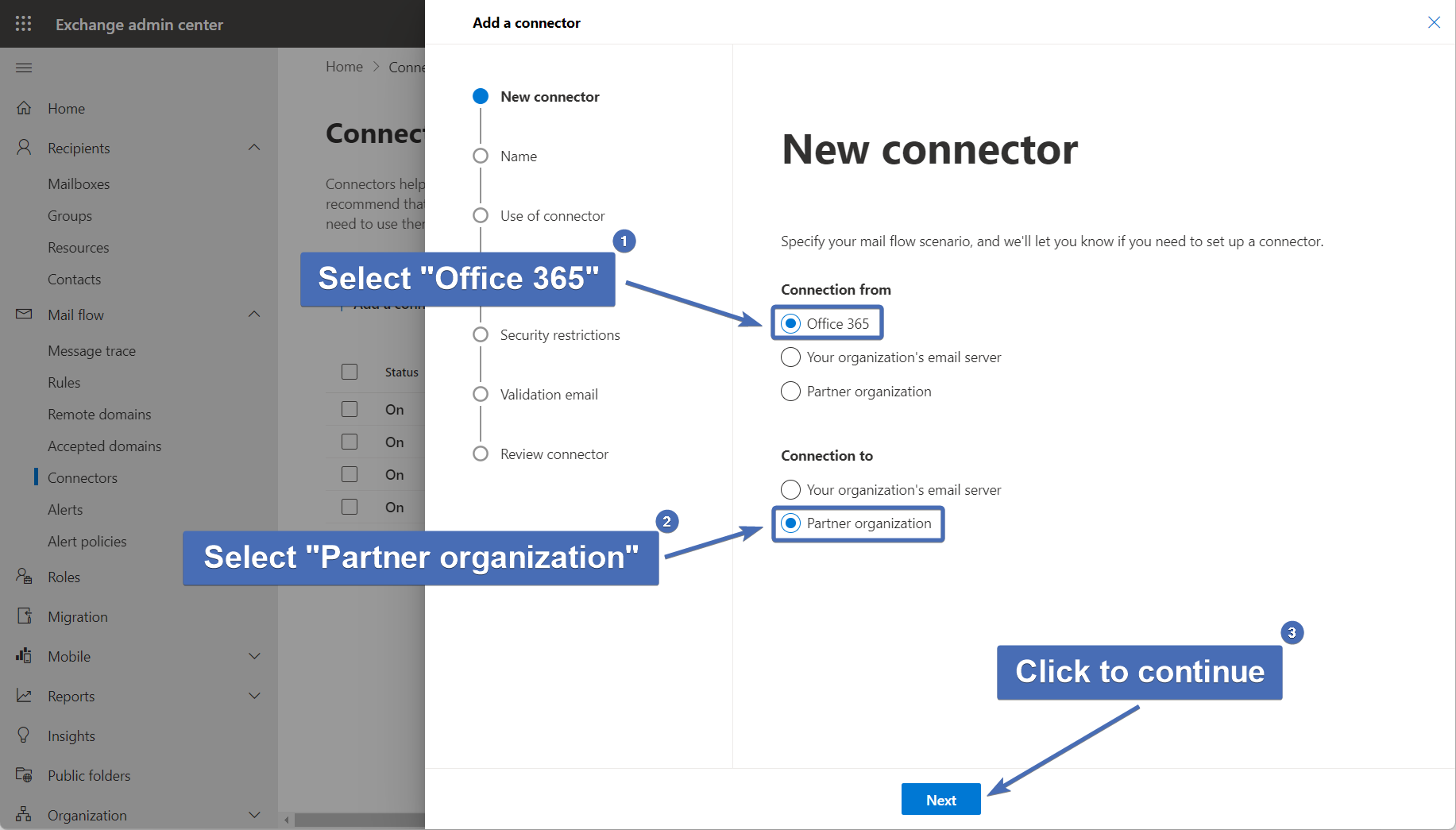
Step 14 – Naming and describing the connector
In the “Name” field enter the following name – “Trustifi Inbound Connector (Send)".
In the "Description" field you can add any description you like (optional). Make sure the "Turn it on" box is checked
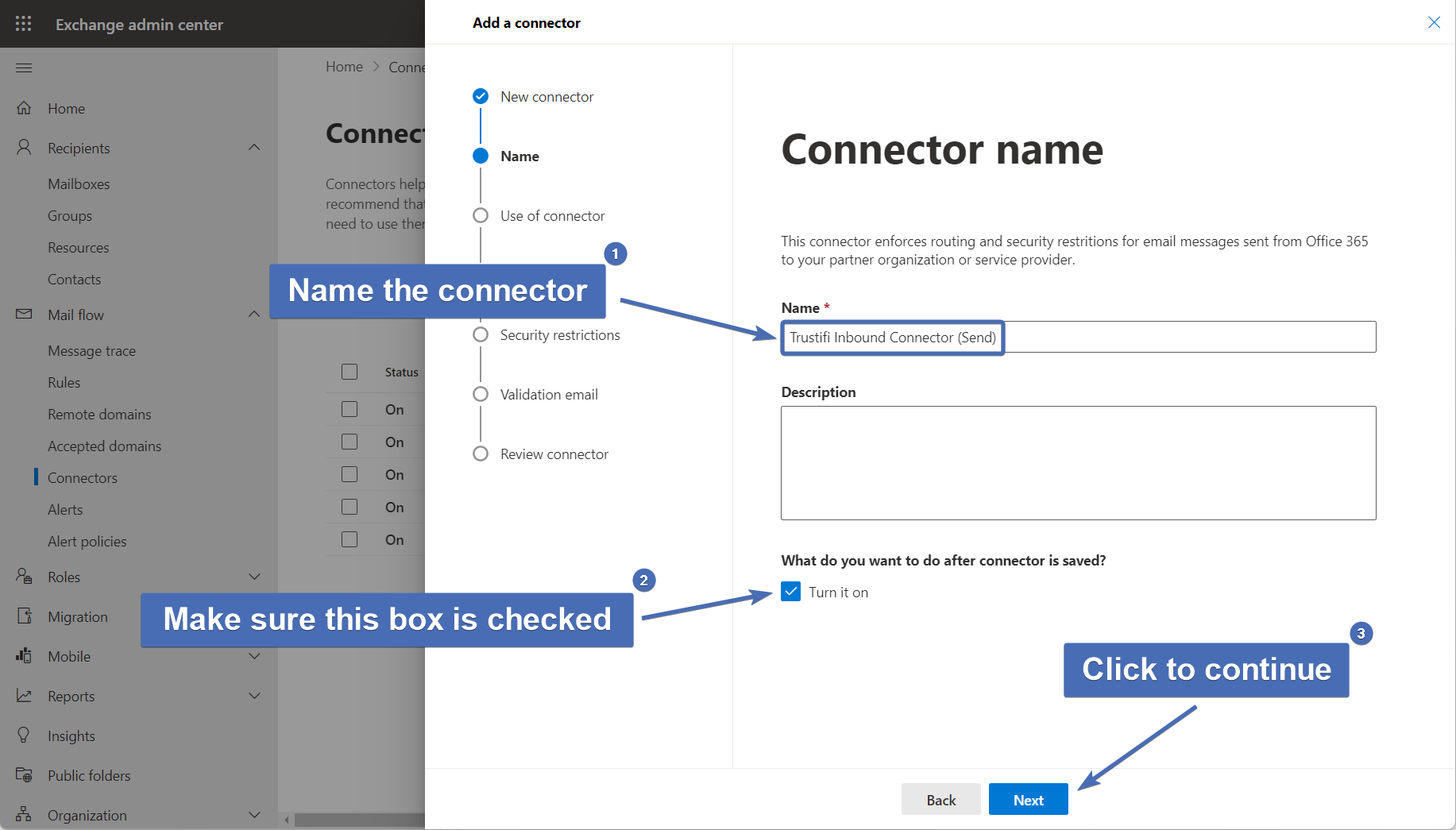
Step 15 – Use of connector
Select “Only when I have transport rule set up that redirects message to this connector” and continue by clicking “Next”
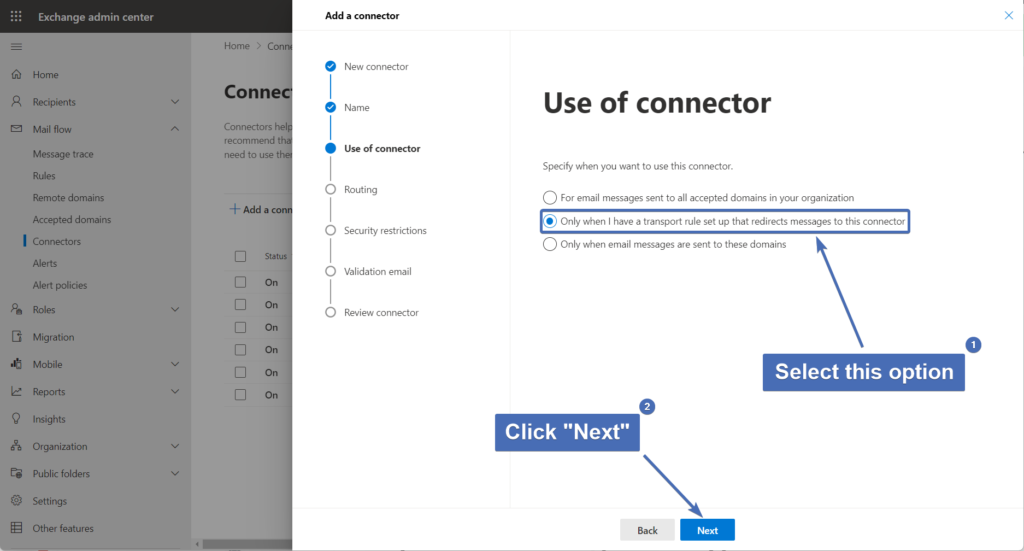
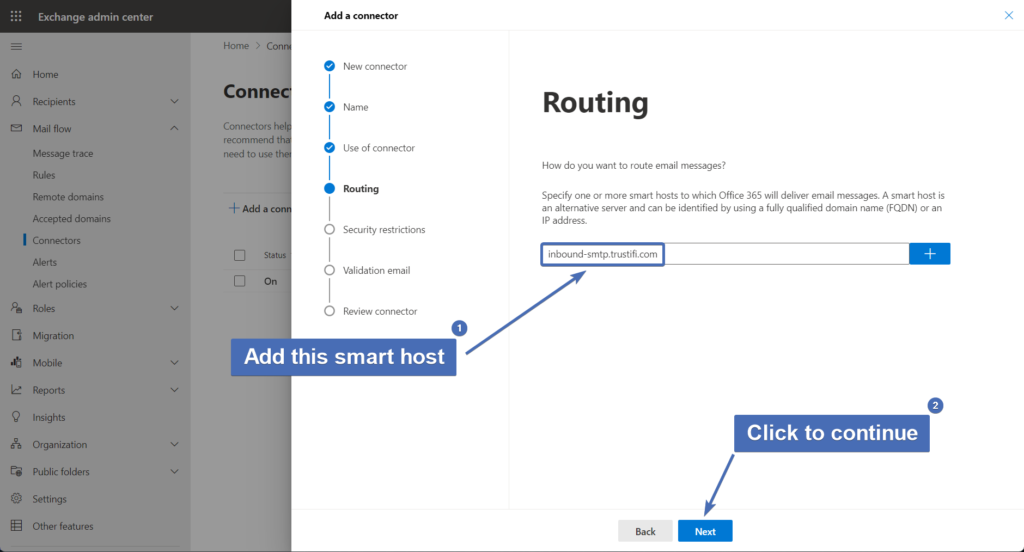
Step 16 – Routing
Here we will need to add the smart host to which emails will be routed.
In the input field, add the following smart host:
inbound-smtp.trustifi.com
Then, click on the "+" icon to add the smart host and click "Next" to continue.
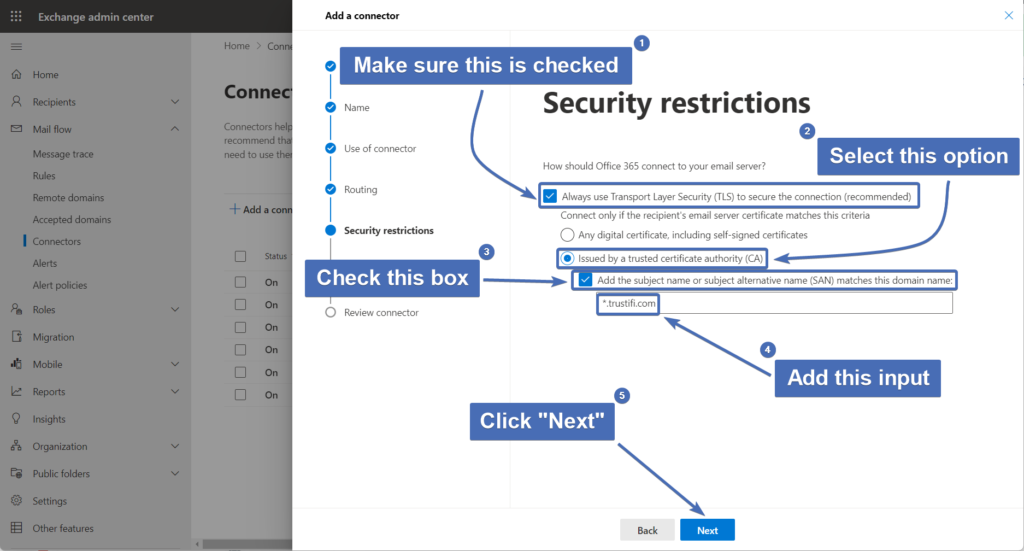
Step 17 – Security restrictions
Now we will need to configure the smart host security settings:
Select “Always use TLS” (First checkbox)
Select “Issued by a trusted certificate authority (CA)”
Check the box for "Add the subject name of subject alternative name (SAN) matches this domain name"
Enter the following value into the input field: *.trustifi.com
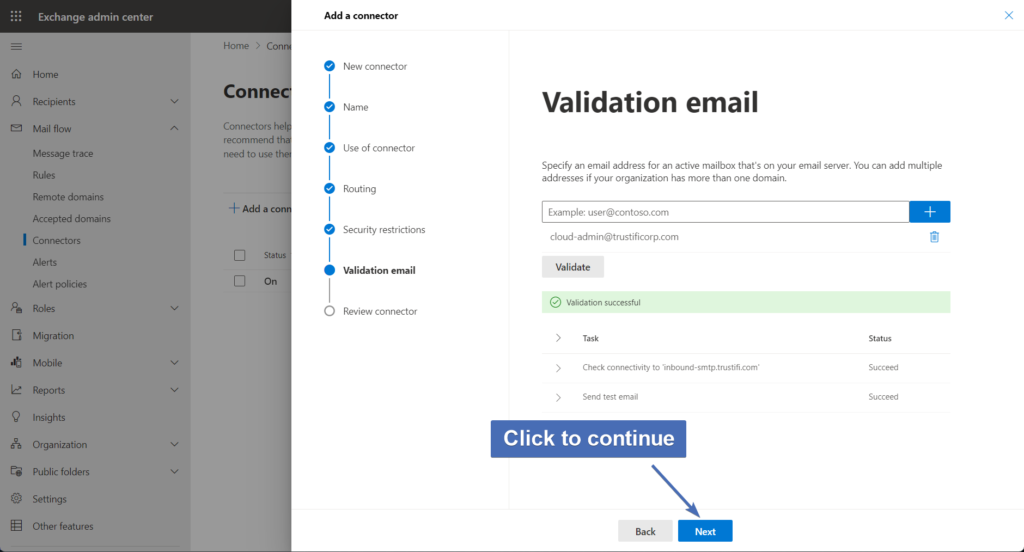
Step 18 – validating the connector
In this step, Exchange will need to validate the connector by sending an email through it. Enter an email for an active mailbox that's on your email server, and click on the "Validate" button.

Step 19 – Validation results
After the connection check is done, a status of "Succeed" or "Failed" will appear for each of the validation tests.
The "Check connectivity" test should succeed. If the status of this test has failed, please check that the smart host address was entered correctly. If the "Send test email" test fails, it's OK. This is because we don't yet have a rule set up to use this connector.
Click on "Next" to continue. You may receive a warning - click "Yes" to confirm and continue.
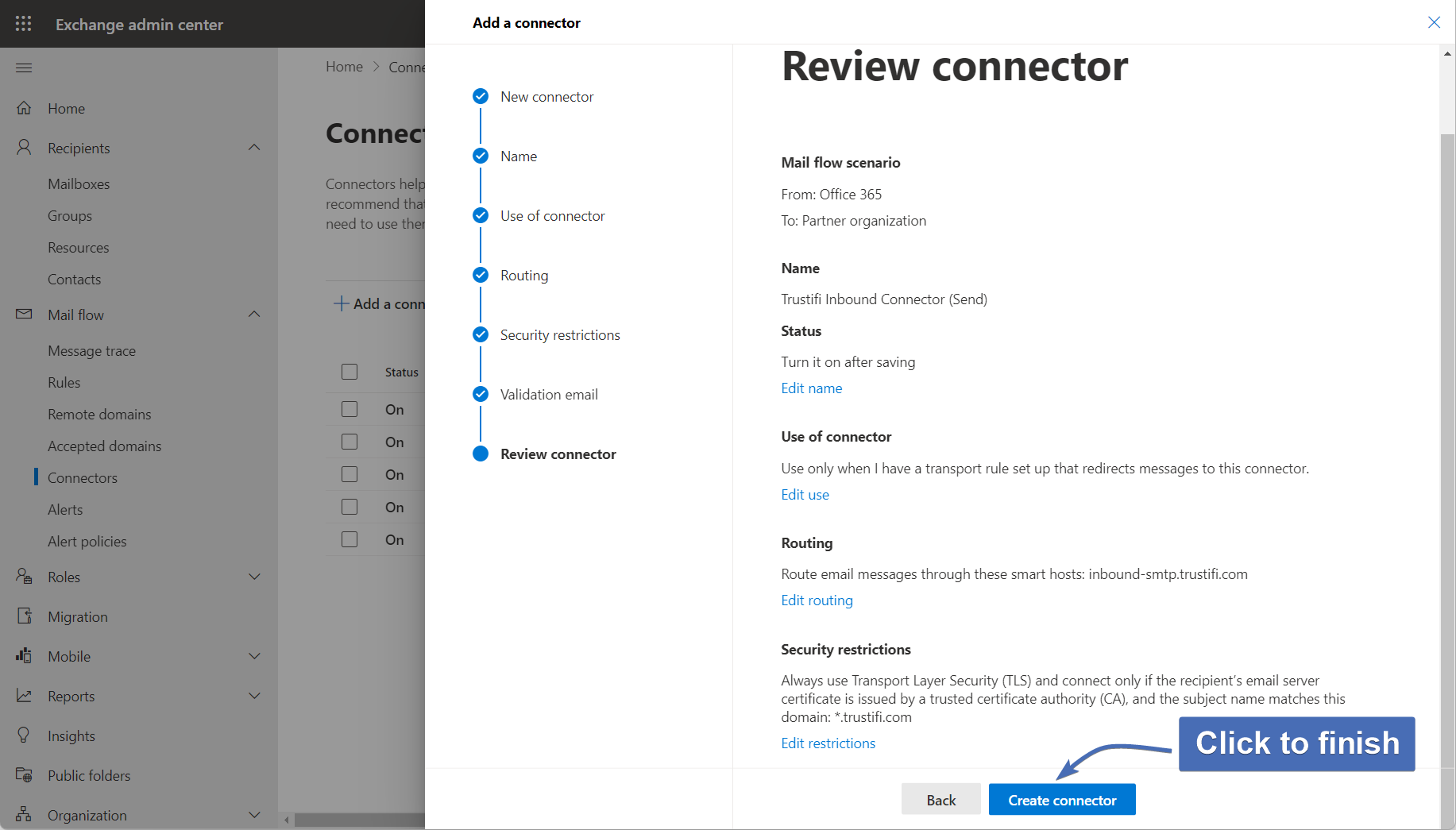
Step 20 - Reviewing the connector
Confirm that all settings are correct and finish by clicking on “Create connector”.
Modifying "Remote domains" settings
Step 21 – Navigating to the remote domains tab and editing the default
Note: For a detailed explanation of the required changes to "Remote domains", please read this article.
In this section, we will make some changes to the "Remote domains" settings. These changes are not strictly mandatory for the process, but will ensure that all types of email content are delivered correctly using Trustifi.
First, go to "Remote domains'" under "Mail flow" and click on the default domain settings.
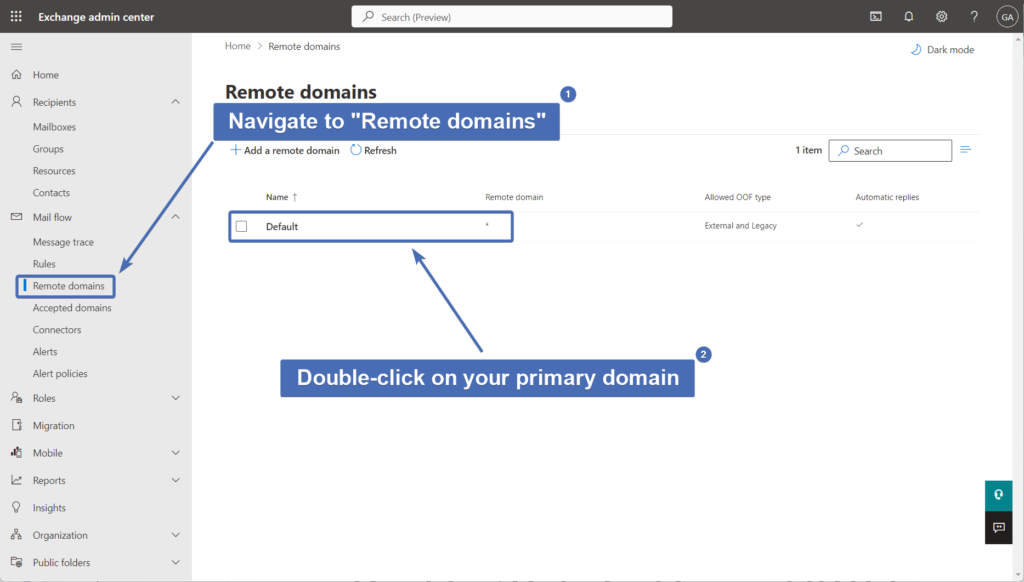
Step 22 – Editing the RTF settings
In the section that includes "Use rich-text format", click on "Edit text and character set".
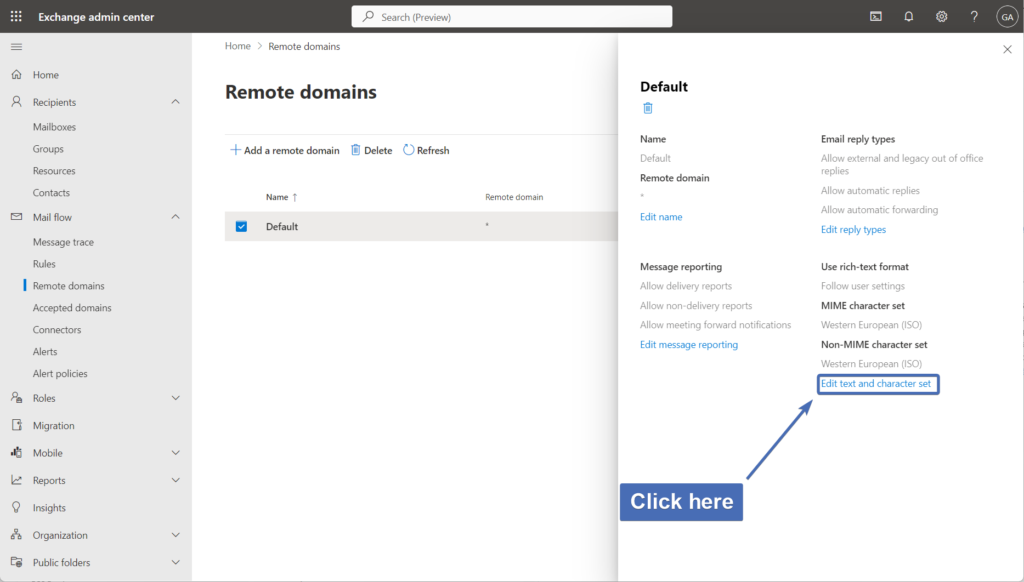
Step 23 – Changing the RTF settings
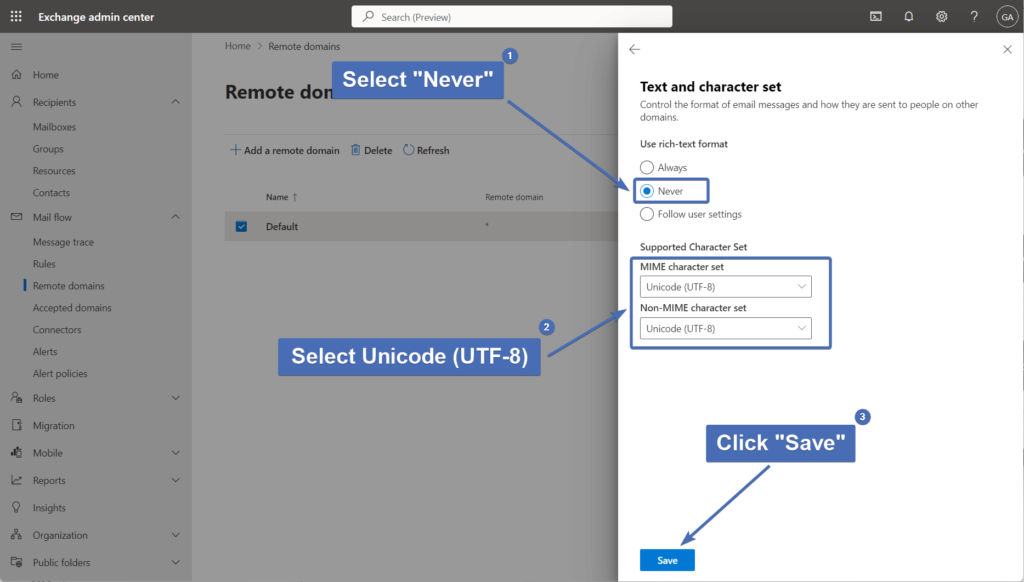
Set the following:
Under "Use Rich Text format"- select "Never"
Under "MIME character set" - select "Unicode (UTF-8)"
Under "Non-MIME character set" - select "Unicode (UTF-8)"
Then, click on "Save".
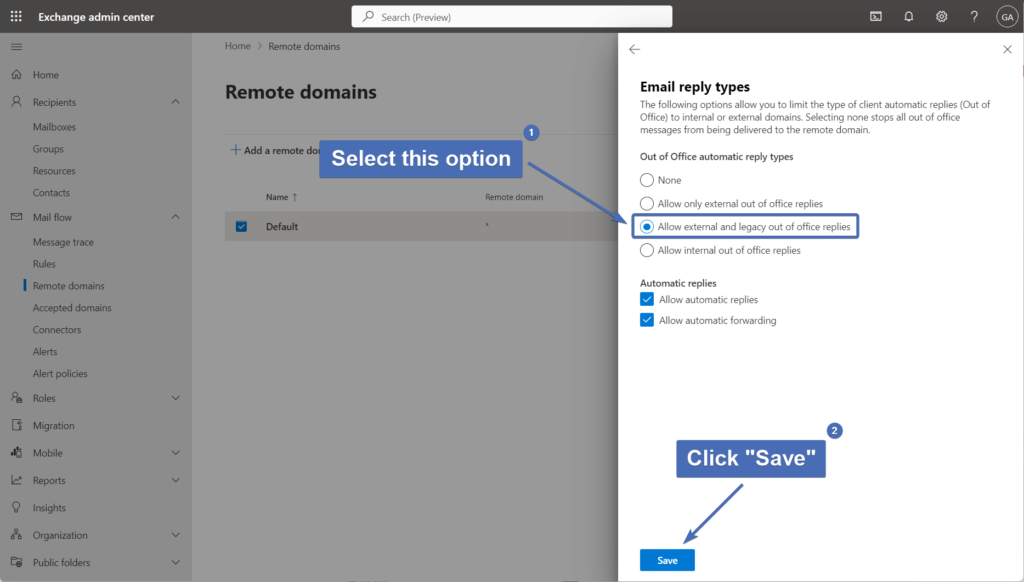
Step 24 - Editing reply types
Under "Email reply types", click on "Edit reply types".
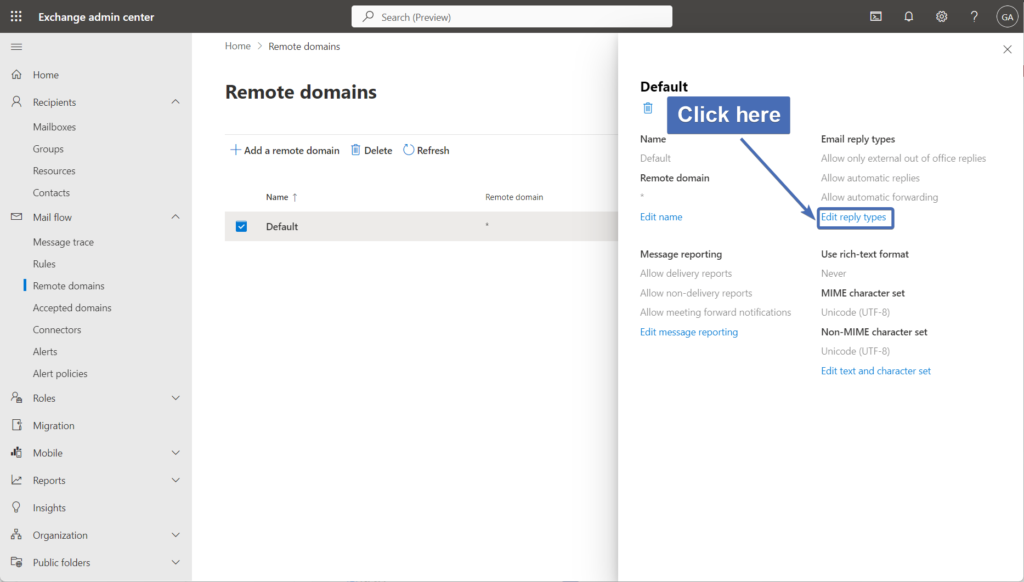
Step 25- Changing reply types
Under "Out of Office automatic reply types" - select "Allow external and legacy out of office replies".
Then, click on "Save".
Checking "Accepted Domains" settings
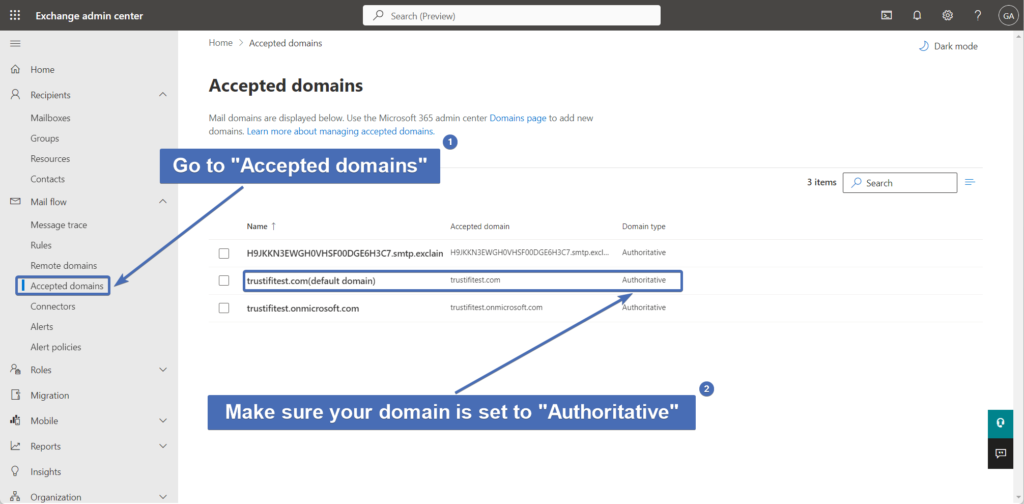
Step 26 – Viewing the "Accepted Domains" settings
First, navigate to "Accepted domains" under "Mail flow".
Find the domain you are configuring the Email Relay for, and verify that the "Domain type" is set to "Authoritative" and not to "Internal relay".
Note: the "Internal relay" configuration is almost always used in situations where the domain has at least one mail server that is not synced with O365. If this is not the situation, the recommended configuration is "Authoritative".
Modifying security settings
In this section we will need to make some modification to the O365 security policies to allow the Trustifi inbound IPs and make sure the emails returning from Trustifi are received successfully.
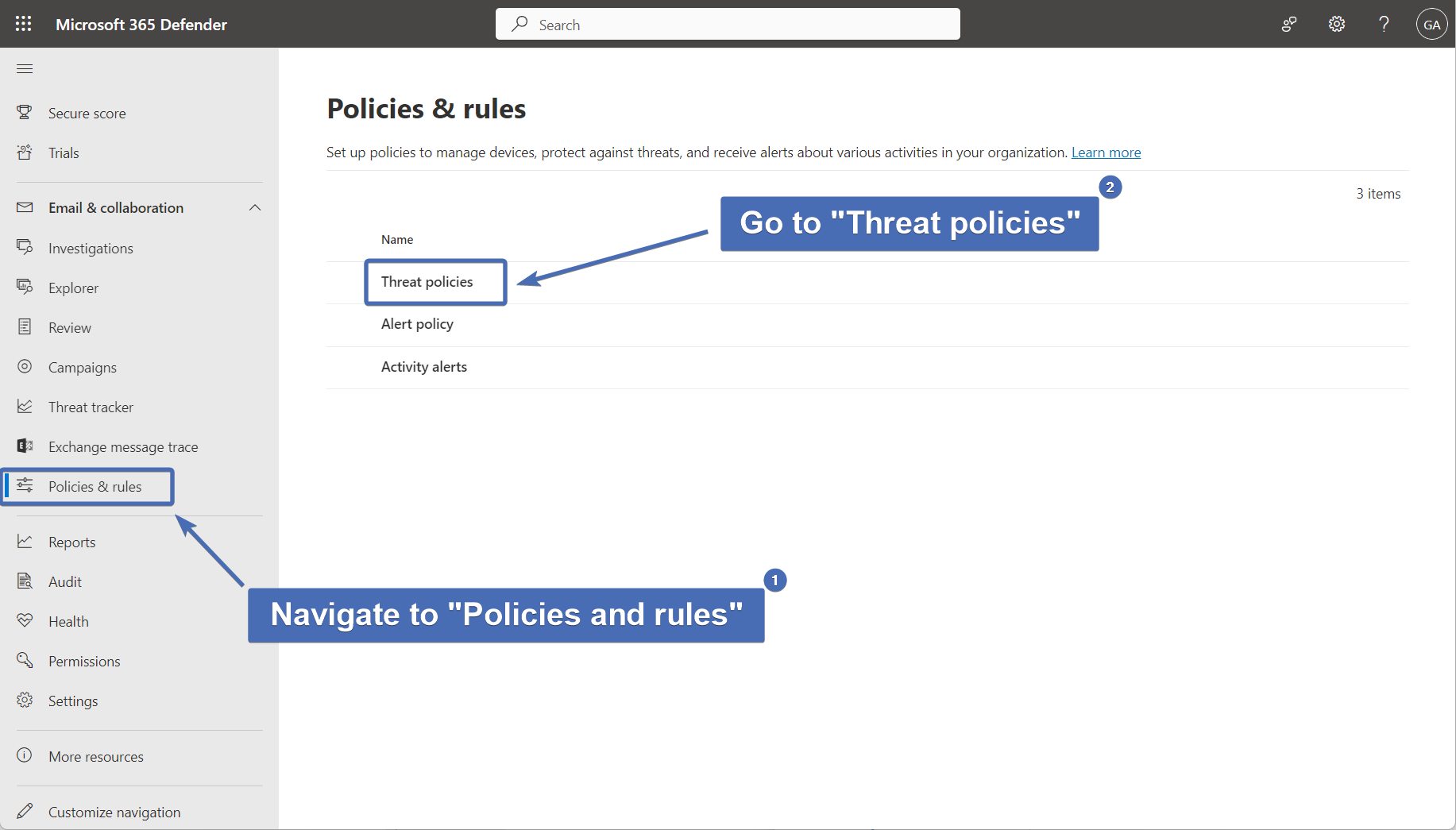
Step 27 – Navigating to "threat policies"
First, log into the O365 security portal.
Then, select "Policies rules" from the left side navigation, and click on "Threat policies".
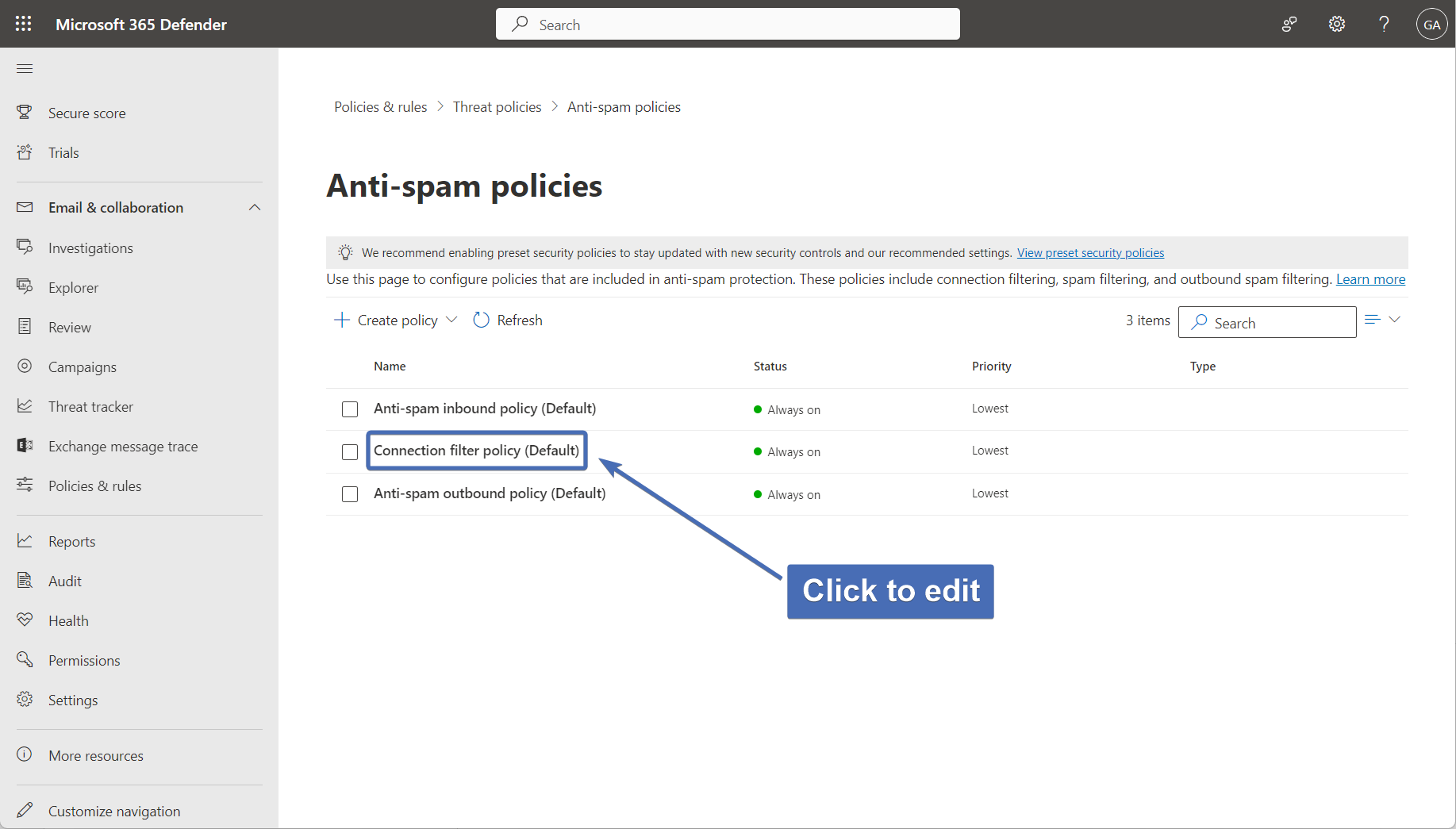
Step 28 – editing the "connection filter policy"
Under "Threat policies", navigate to "Anti-spam policies" and click on "Connection filter policy (default)" to edit.
Step 29 – enabling safe list and adding Trustifi IPs
In the pop-up, first click on "Edit connection filter policy".
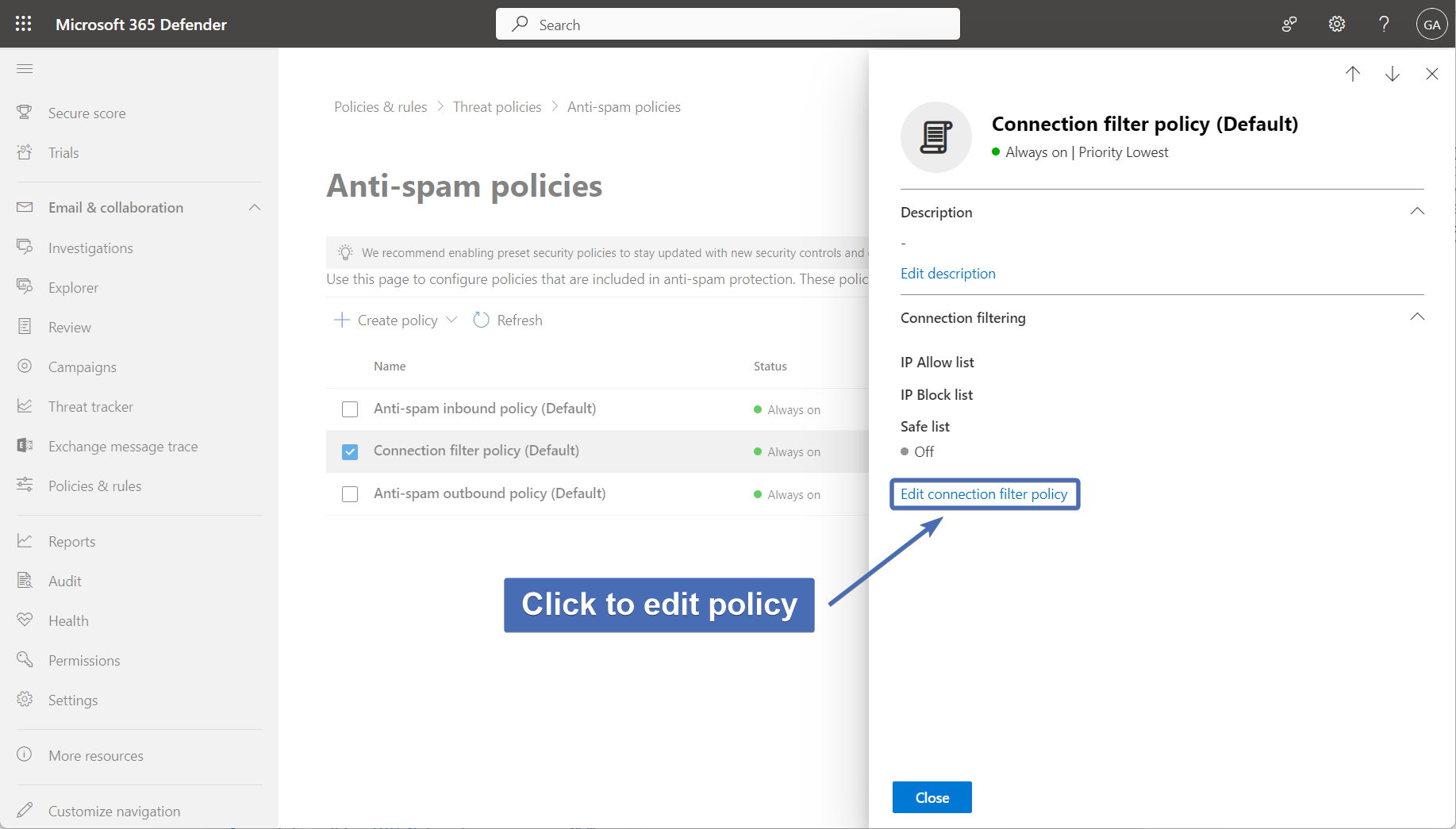
Then, click on "Turn on safe list" and add the following Trustifi IPs to the top section ("Always allow messages from the following IP addresses or IP address range"):
3.93.243.176
3.93.139.220
3.251.32.127
54.195.145.1
52.89.220.23
52.37.228.167
52.54.159.237
52.73.143.252
3.221.25.19
34.192.117.166
44.209.231.3
35.172.145.174
After the Trustifi IPs have been added, click on "Save".
.png)
Step 30 – navigating to "tenant allow/block lists"
Return to the "Threat policies" page, scroll down to the "Rules" section, and click on "Tenant allow/block lists".
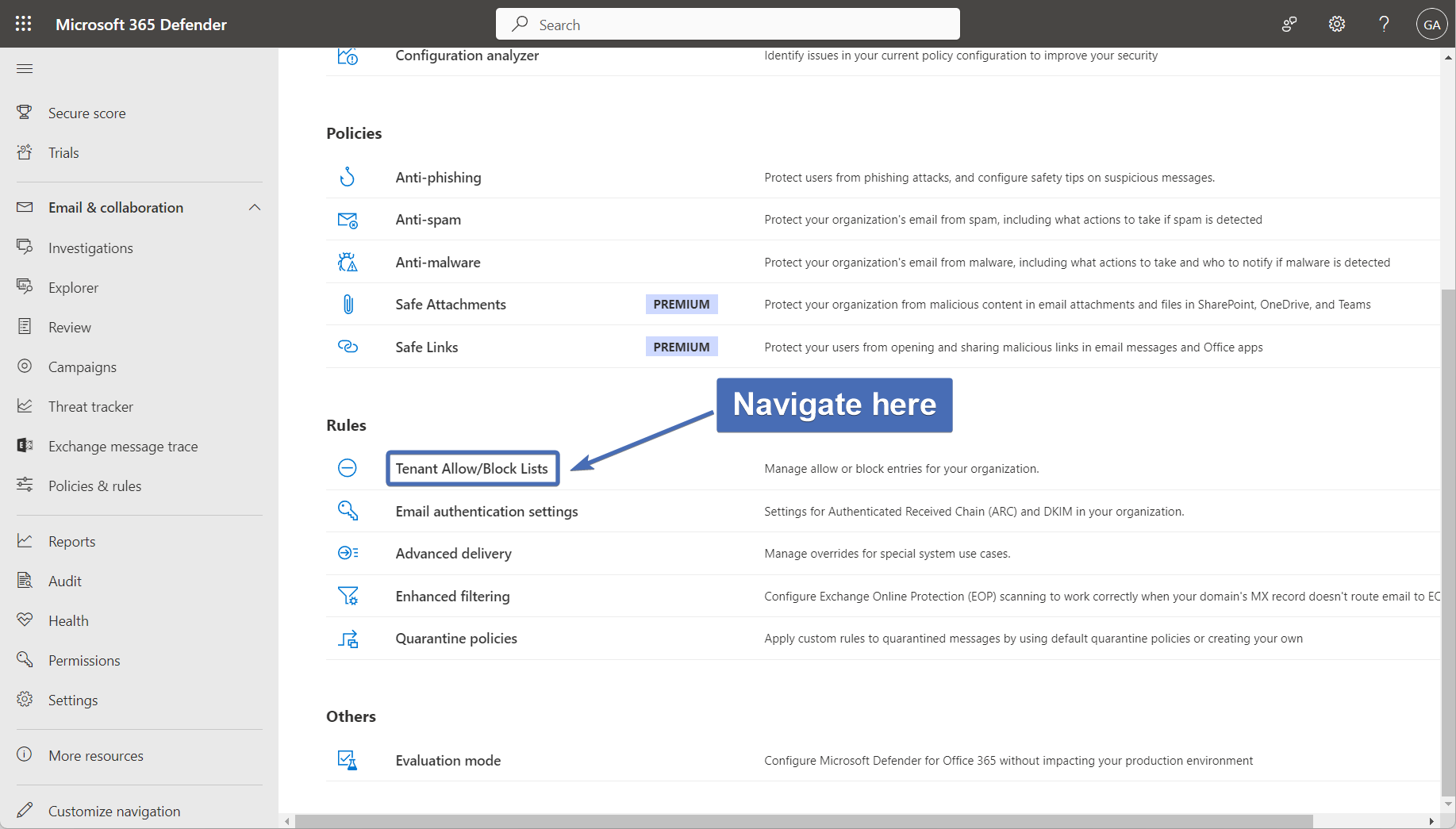
Step 31 – Adding an allow list
Under "Tenant allow/block lists", click on the "Spoofed senders" tab and then click on the "Add" button to add an allow list.
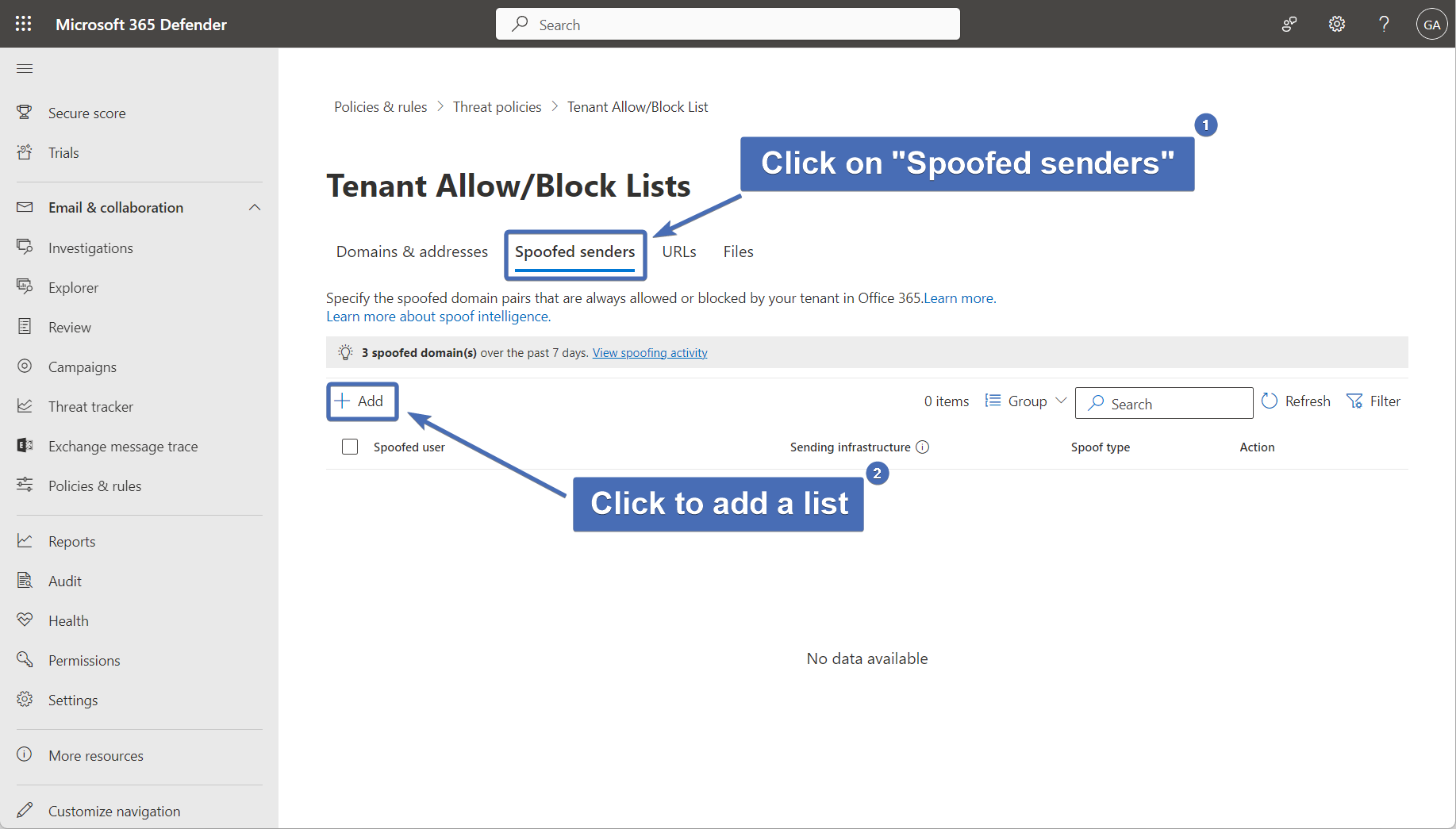
Step 32 – Configuring the internal allow list
In the pop-up, perform these actions:
Add the Trustifi IPs in the following format: wildcard (asterisk), then comma, then a space and the IP. For example:
*, 3.93.243.176
Add each Trustifi IP like this in a new line. Screenshot below.
Note: Once all the IPs have been added, copy all of the rows since we will be creating a similar policy in the next step.Under "Spoof type", select "Internal".
Under "Action", select "Allow".
Click on "Add" to finish.
Step 33 – Configuring the external allow list
Click on the "Add" button to add a new allow list. In the pop-up, perform the same steps as before with one exception:
In the "Spoof type" section, select "External" instead of "Internal".
Creating a mail flow rule
Step 34 – Creating a new rule
Now we will need to create a new rule to use the connector.
First, go back to the Exchange admin center and navigate to the "Rules" page under "Mail flow".
Then click on "Add a rule".
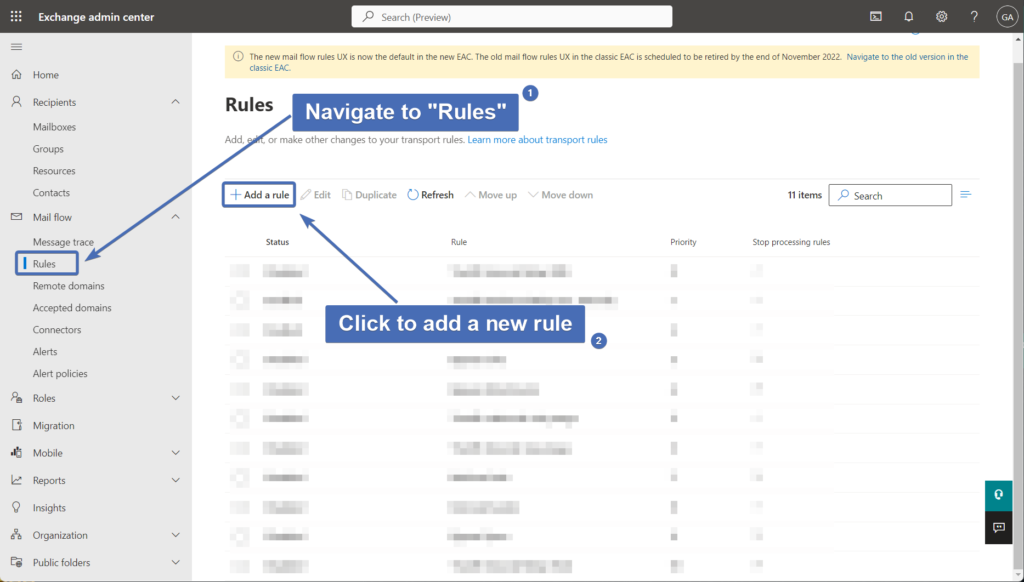
Step 35 – Naming the rule
First, name the new mail flow rule that will be used for the Trustifi inbound relay.
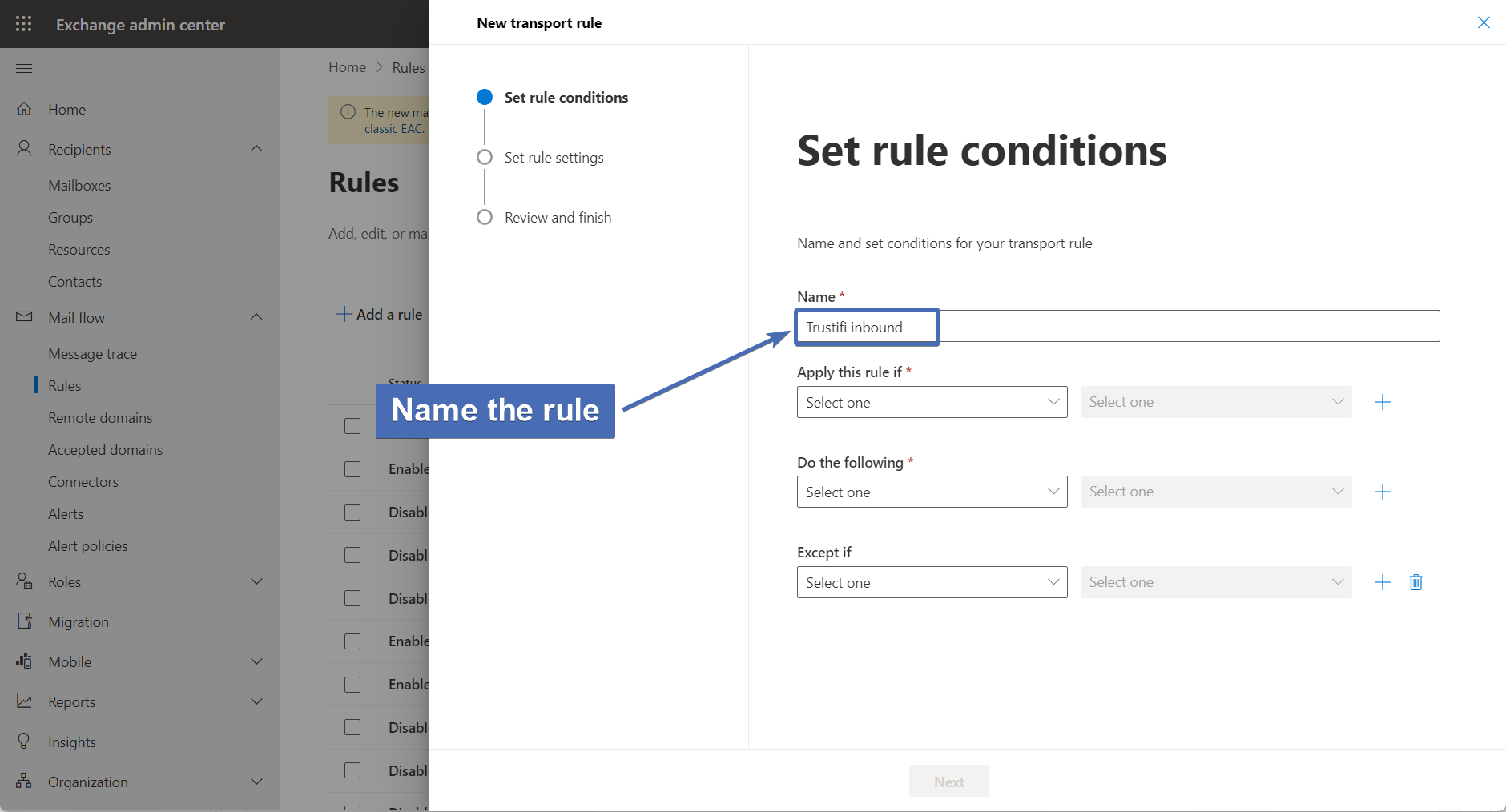
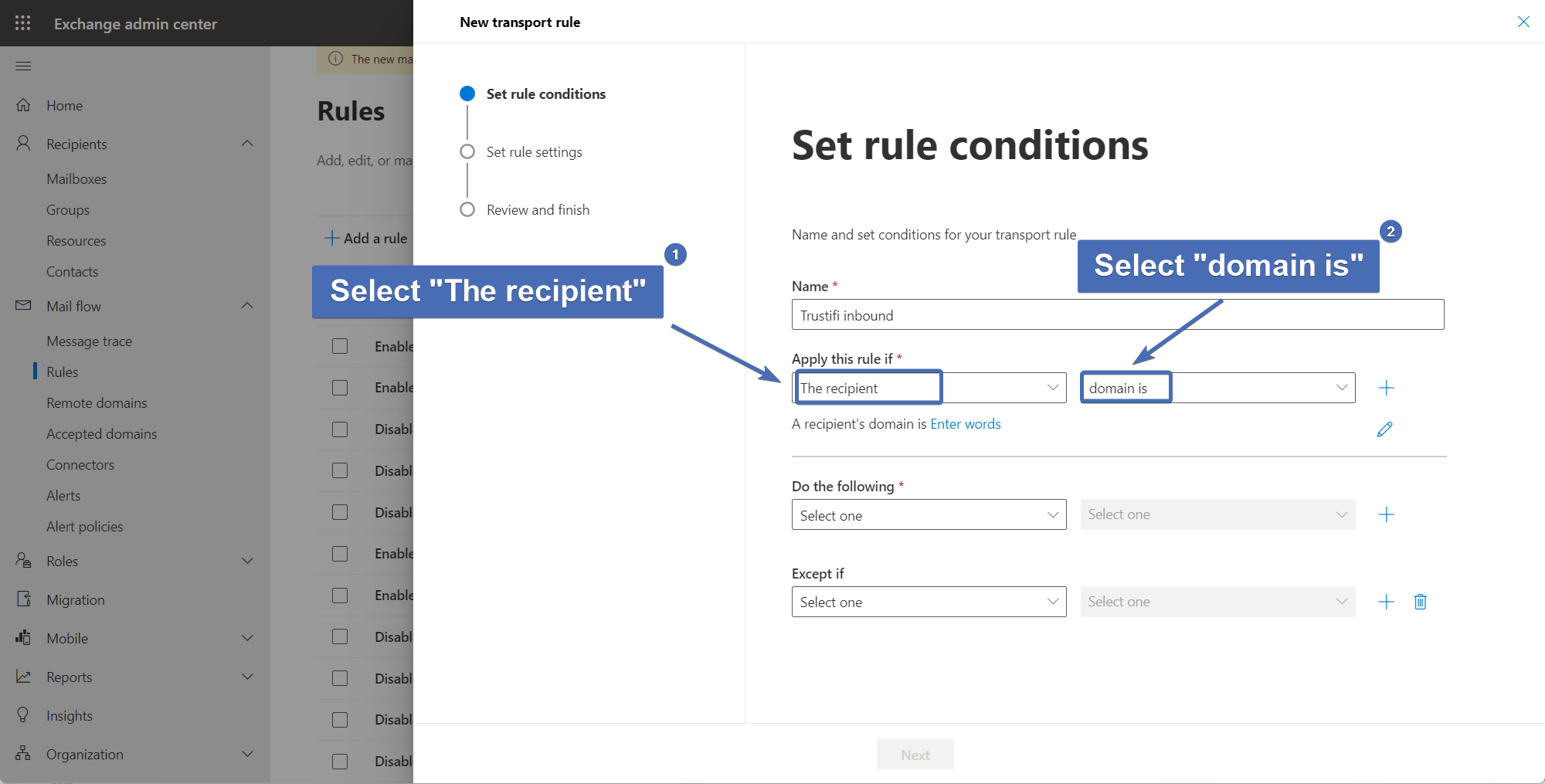
Step 36 – First condition: recipient domain
Under "Apply this rule if", select "The recipient". Then, in the 2nd menu, select "domain is".
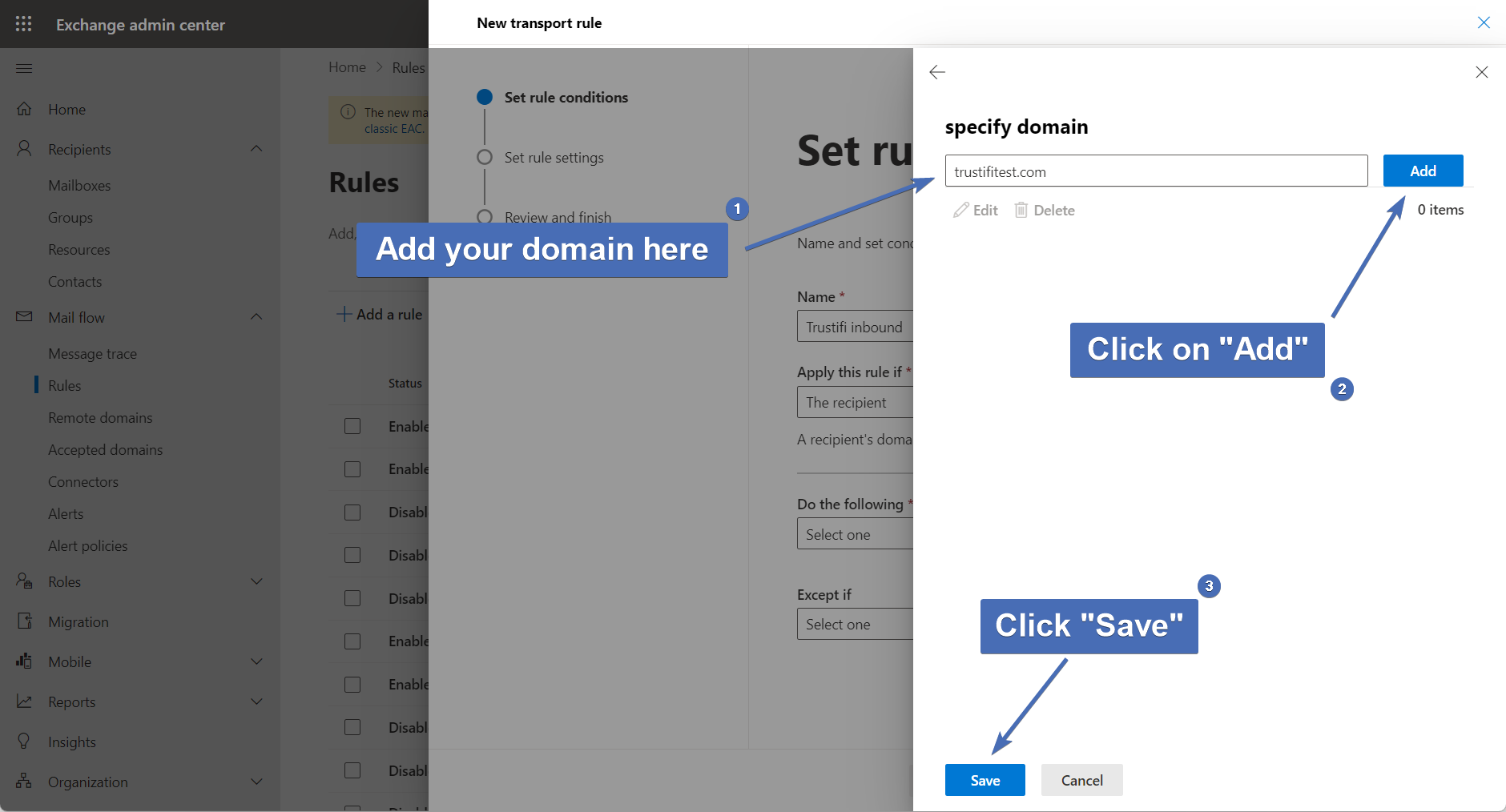
Step 37 – Selecting the recipient domain
Add the domain that will be used to receive emails through Trustifi Email Relay. If you have multiple domains under your tenant, add them all here.
After the domain has been added, click on "Save".
Step 38 – Adding a new condition
Add a new condition by clicking on the "+" icon next to the first condition.
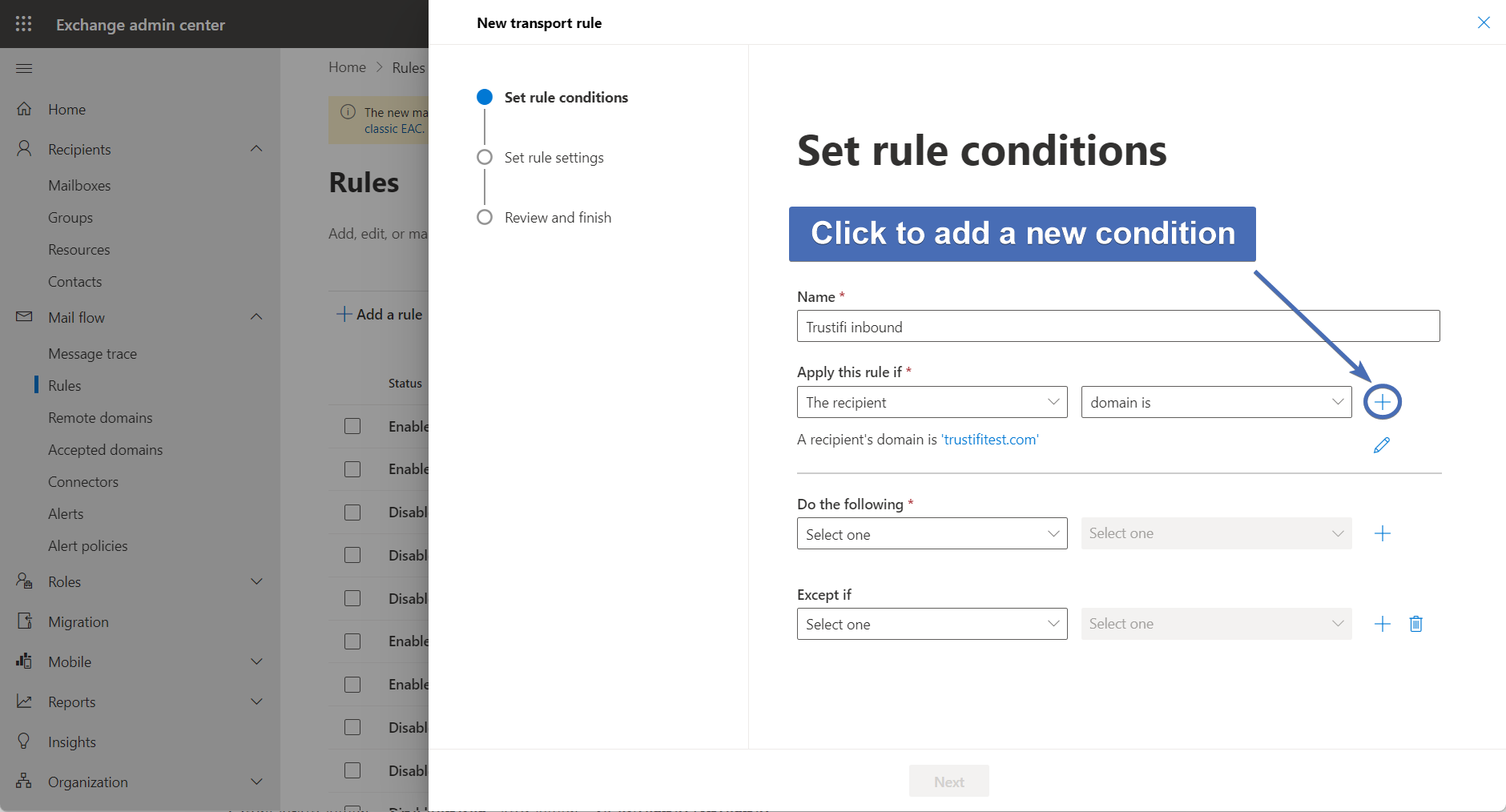
Step 39 – Second condition: recipient location
Once again select “The recipient” and then select “Is external/internal”.
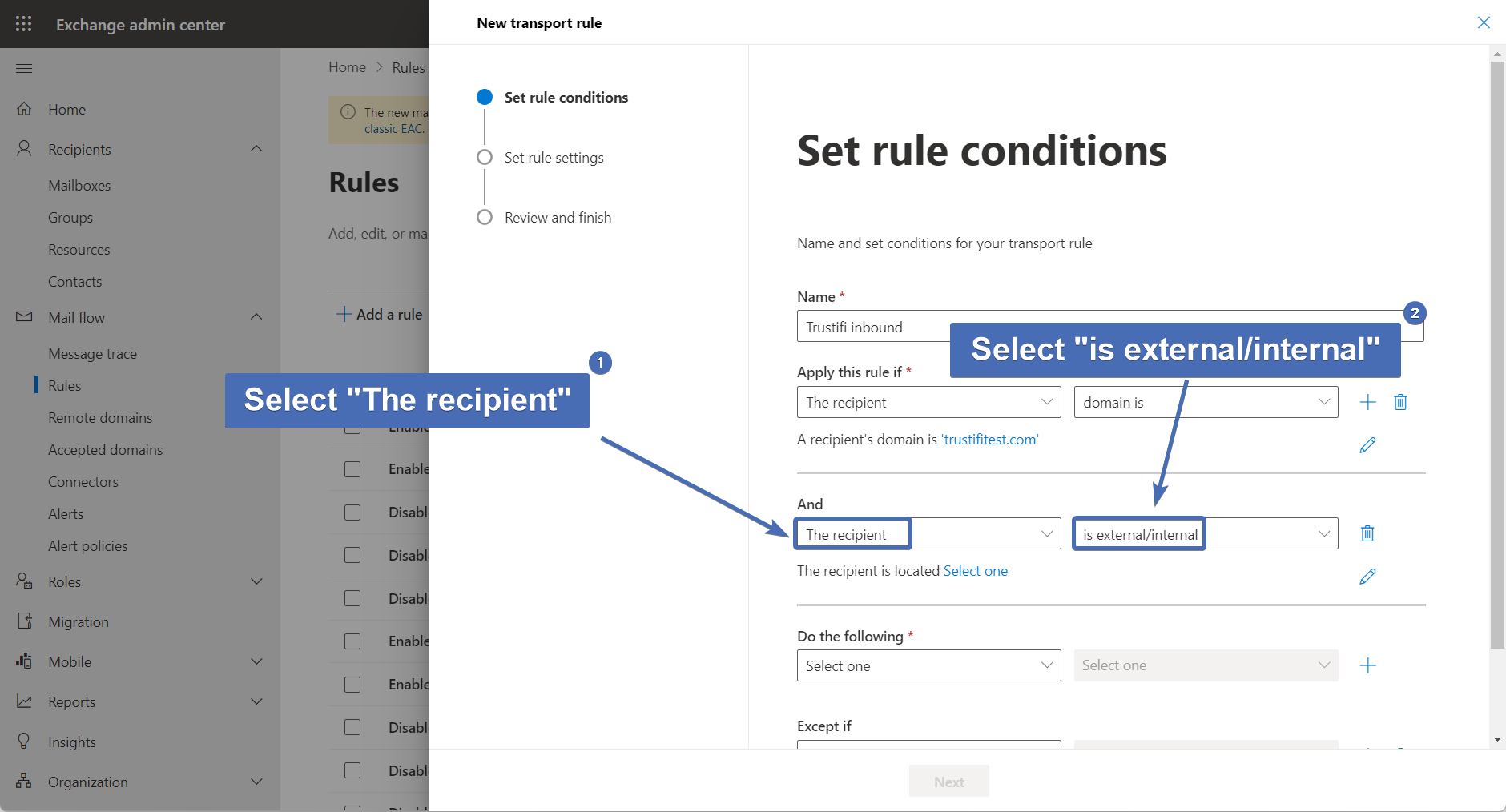
Step 40 – Selecting recipient location
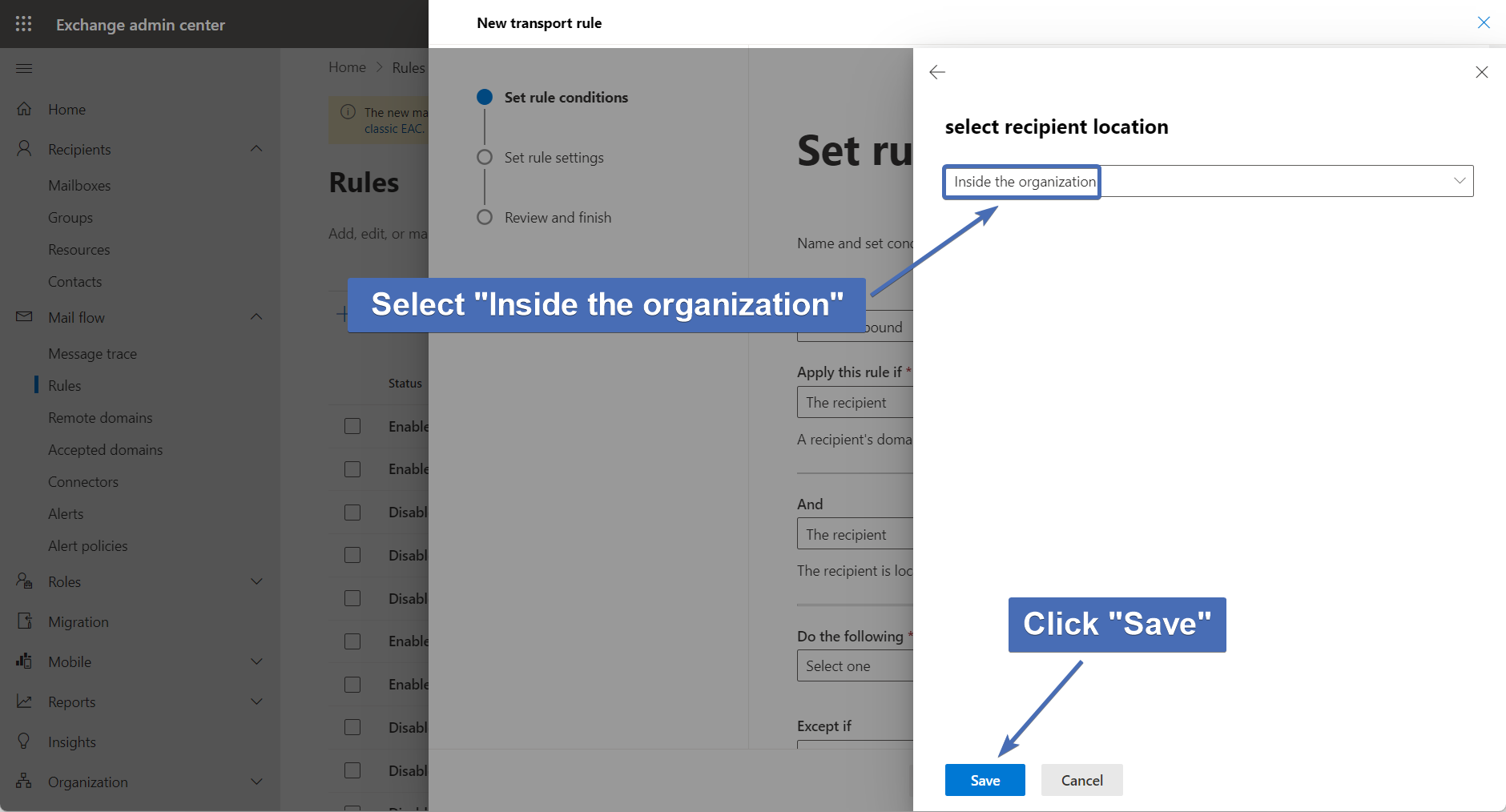
Under "Select sender location", choose "Inside the organization".
Then, click on "Save".
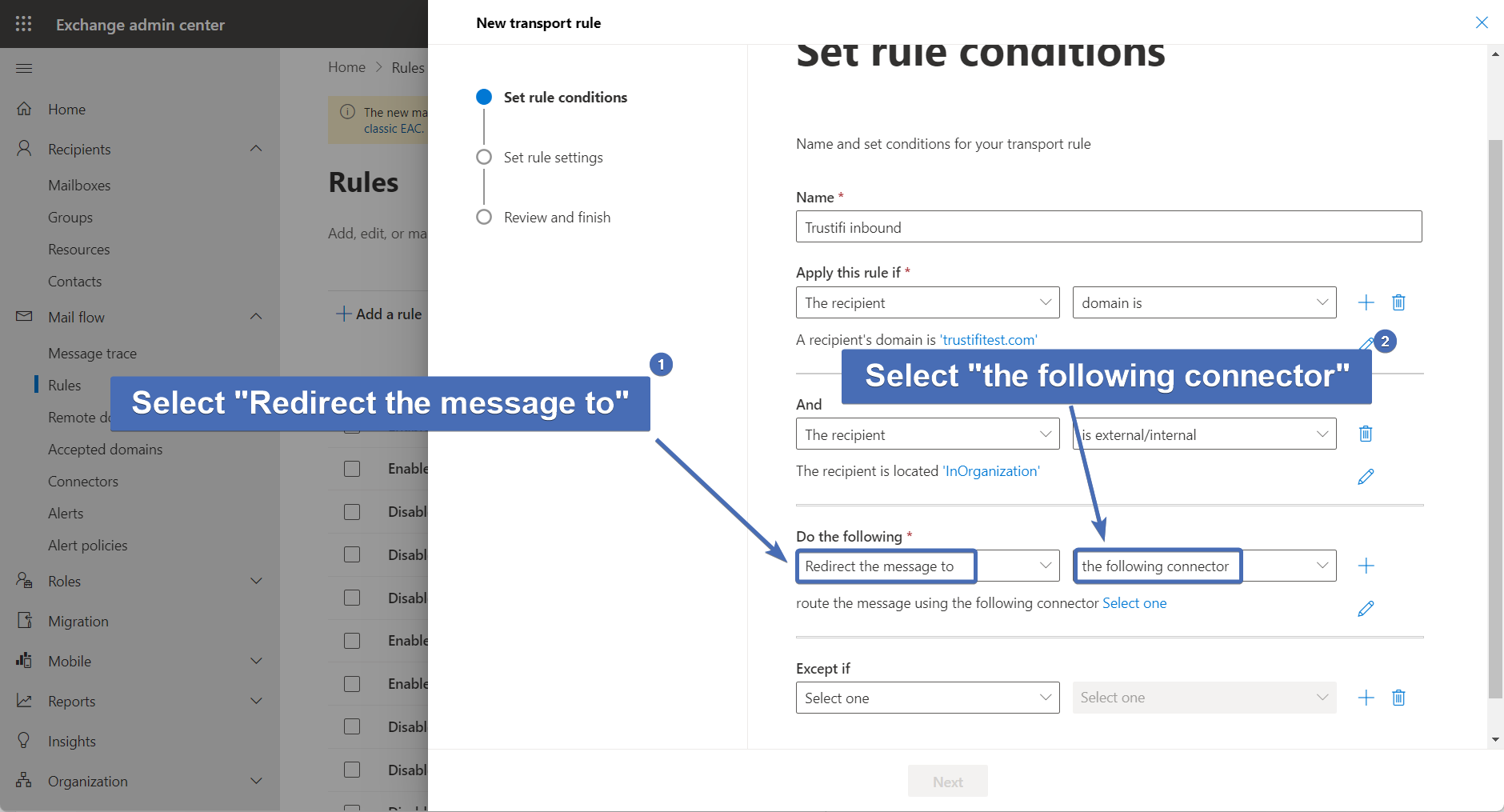
Step 41 – First action: redirect to connector
Now we will start selecting the actions to be taken by this rule.
Under "Do the following" - select "Redirect the message to" and then select "the following connector".
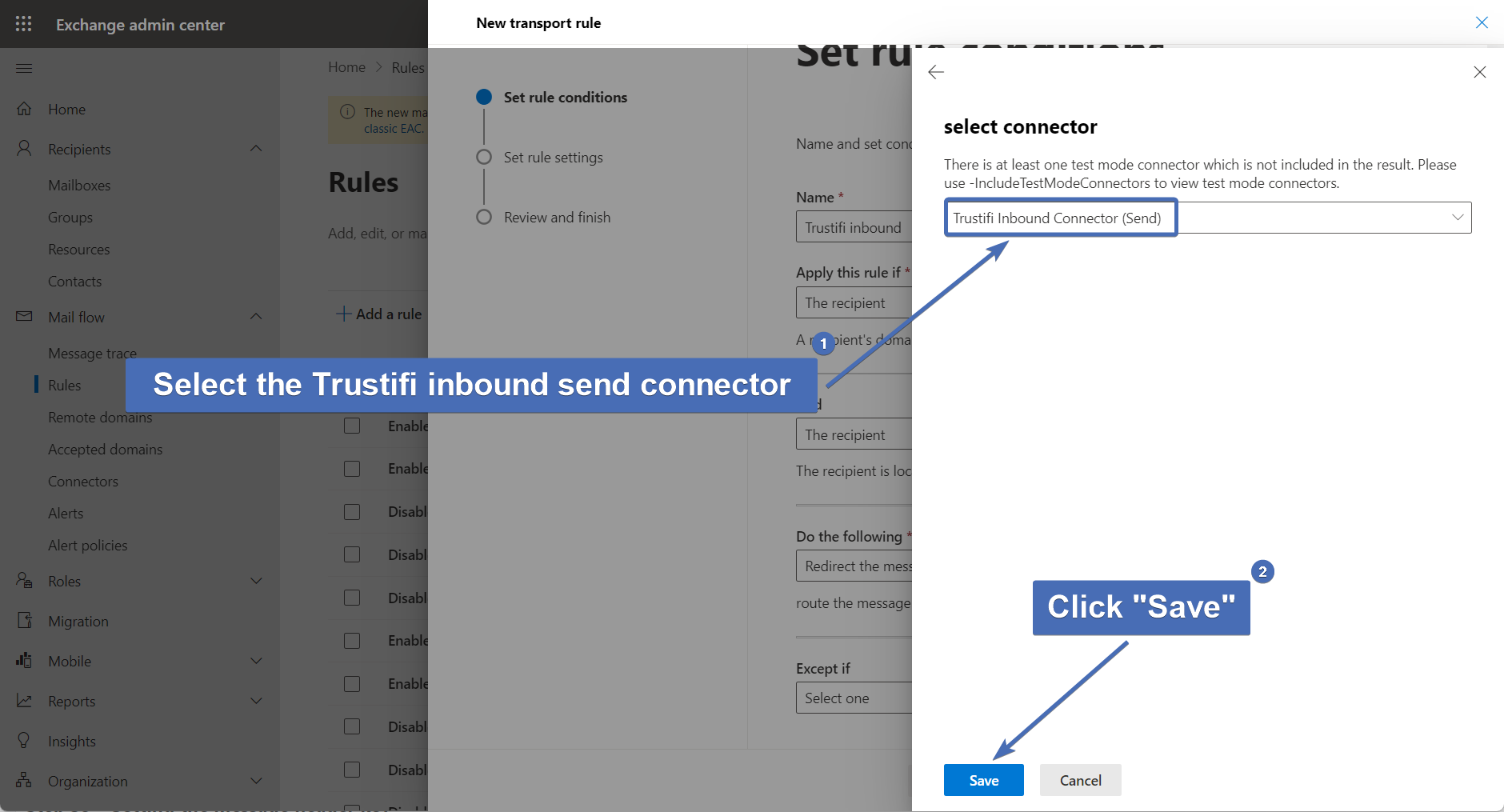
Step 42 – Selecting connector redirection
Under "Select connector", choose the Trustifi inbound send connector which was created earlier.
Then, click on "Save".
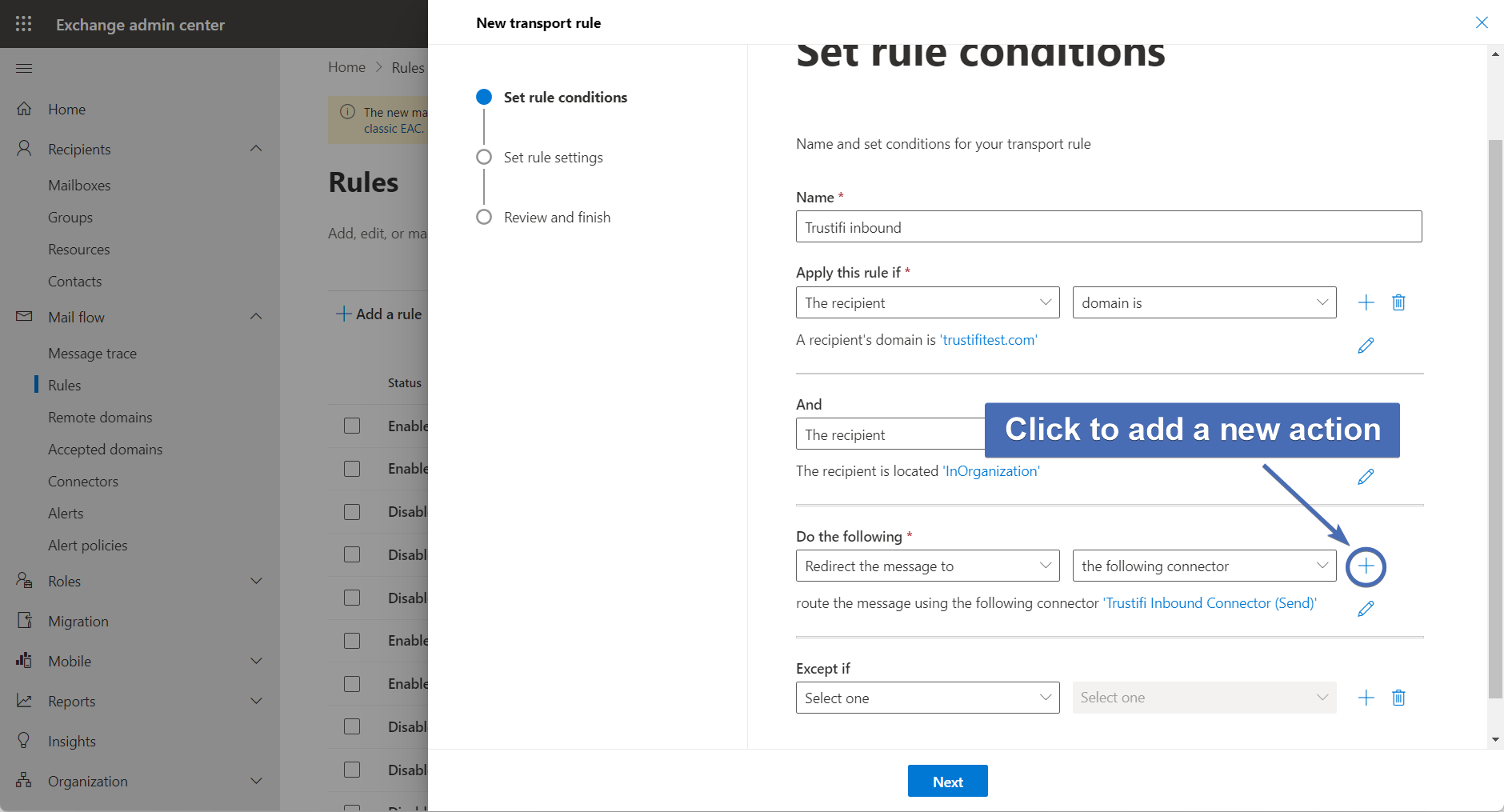
Step 43 – Adding a new action
Add new action by clicking on the "+" icon next to the first action.
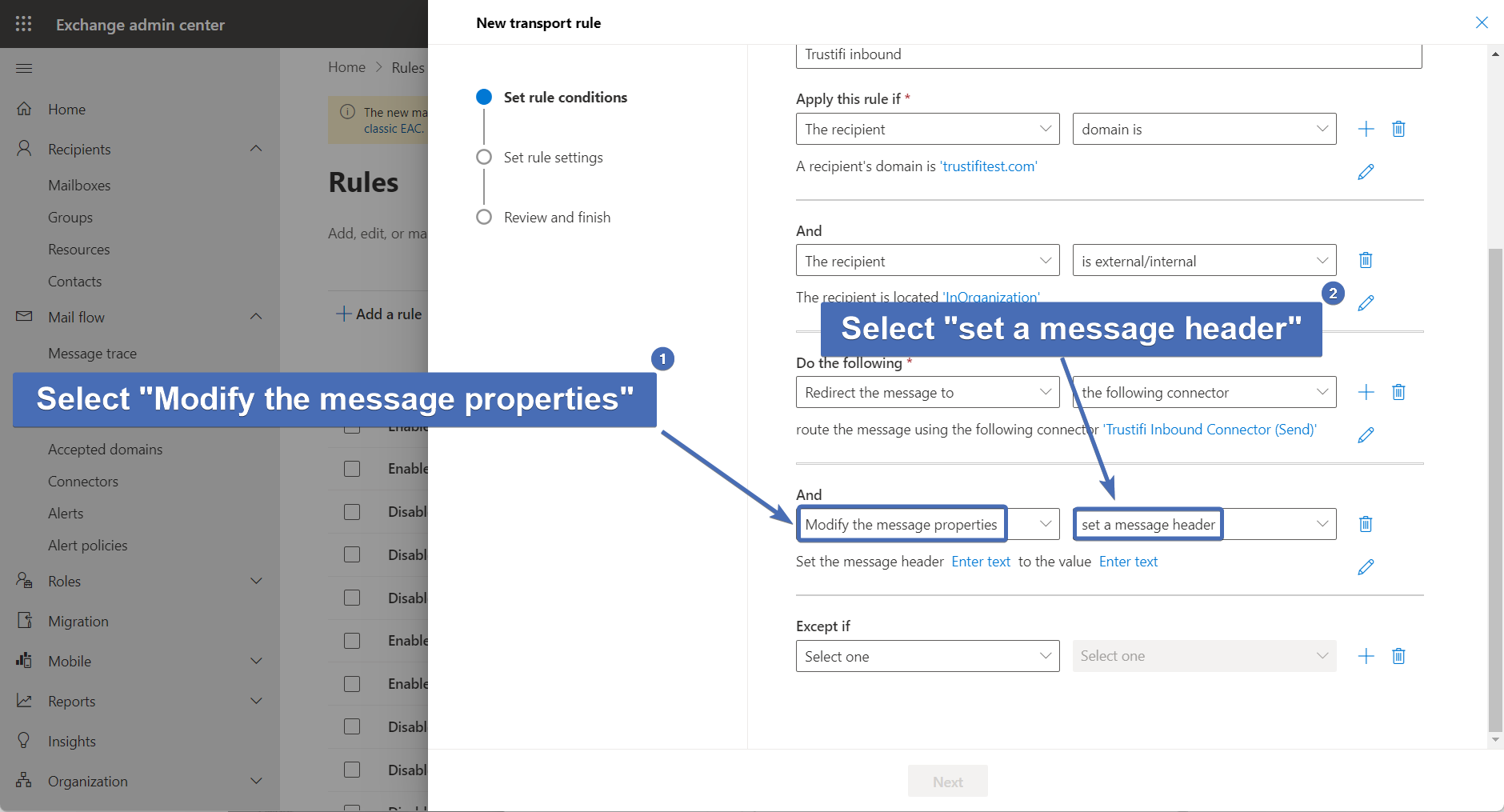
Step 44 – Second action: set a message header
For the new action, select "Modify the message properties" and then select "set a message header".
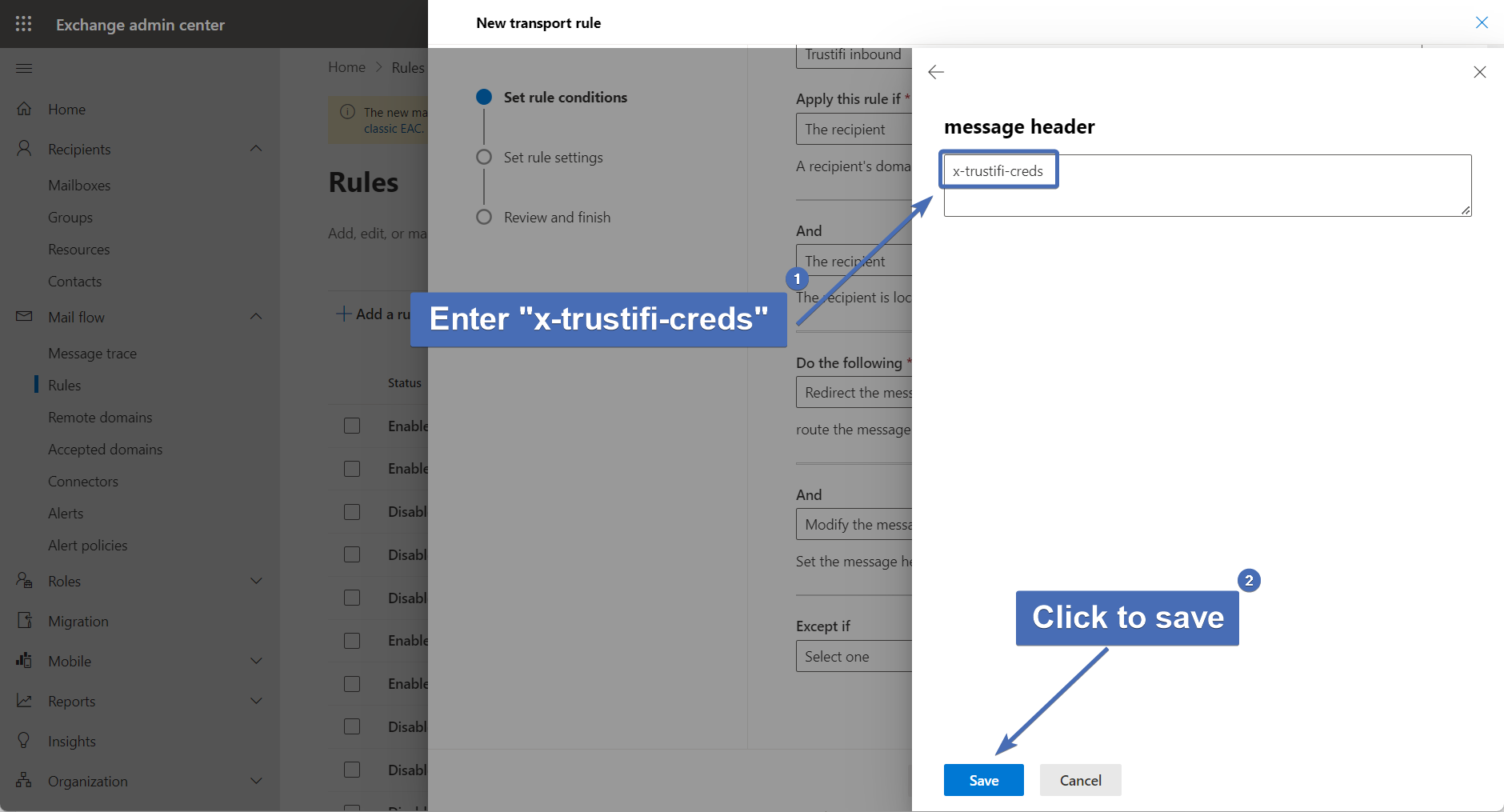
Step 45 – Setting the header name
Click on the first "Enter text" link and add the following input: x-trustifi-creds
Then, click on "Save".
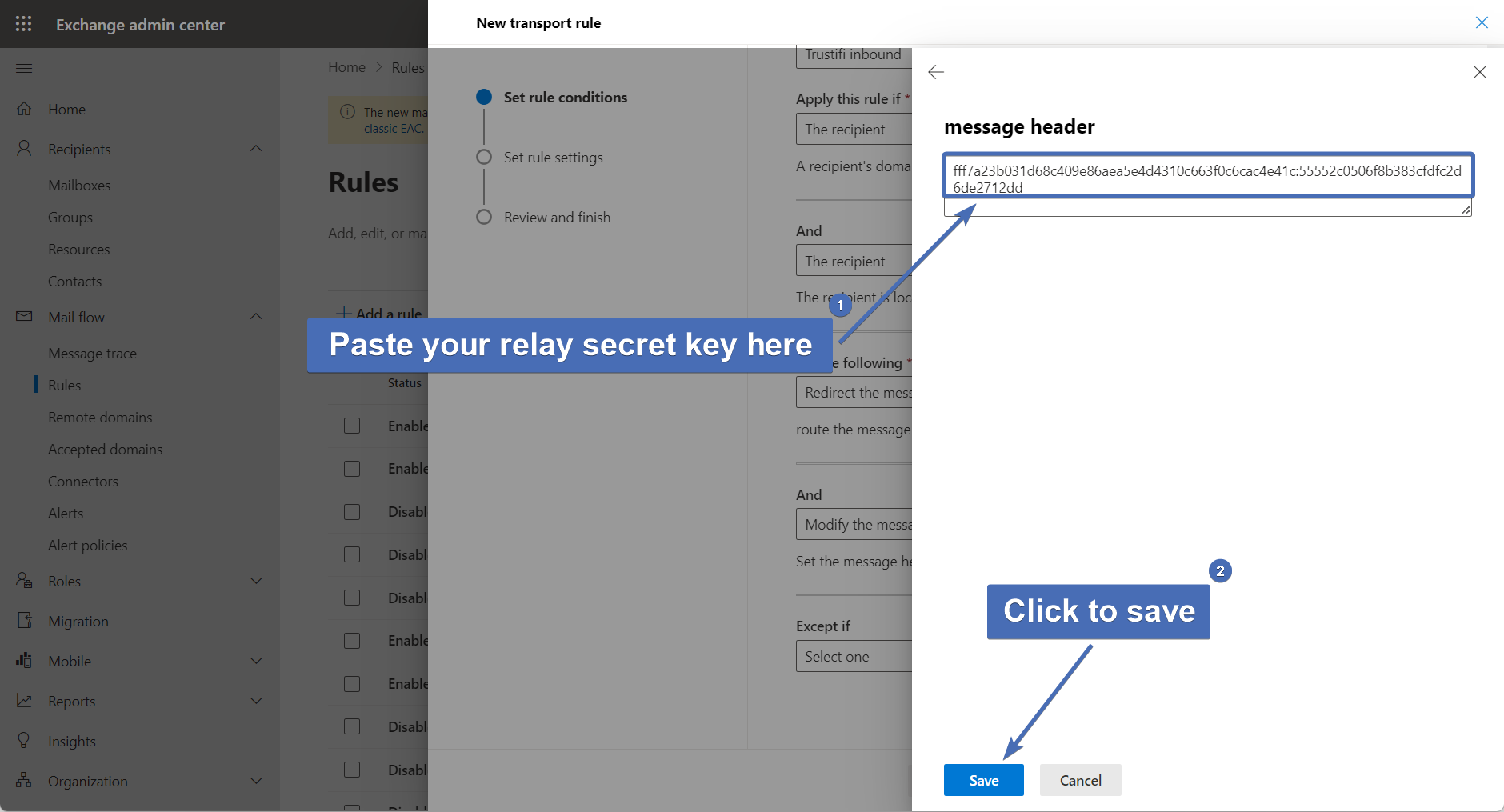
Step 46 – Setting the header value
Click on the second "Enter text" link, and there add the email relay secret key which you copied in step 3.
Then, click on "Save".
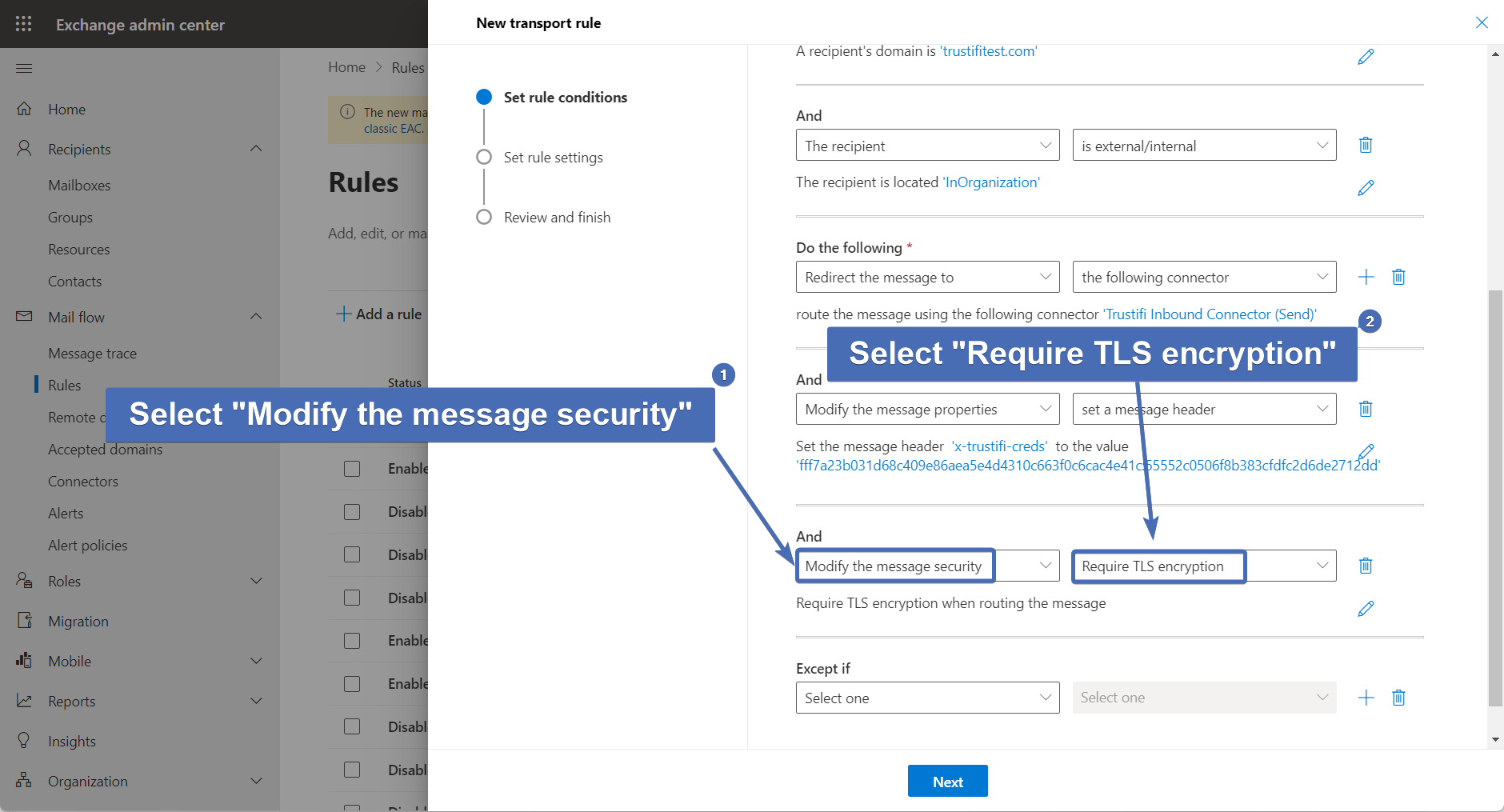
Step 47 – Third action: Require TLS encryption
First, add a new action for the rule. Then select "Modify the message security" and "Require TLS encryption".
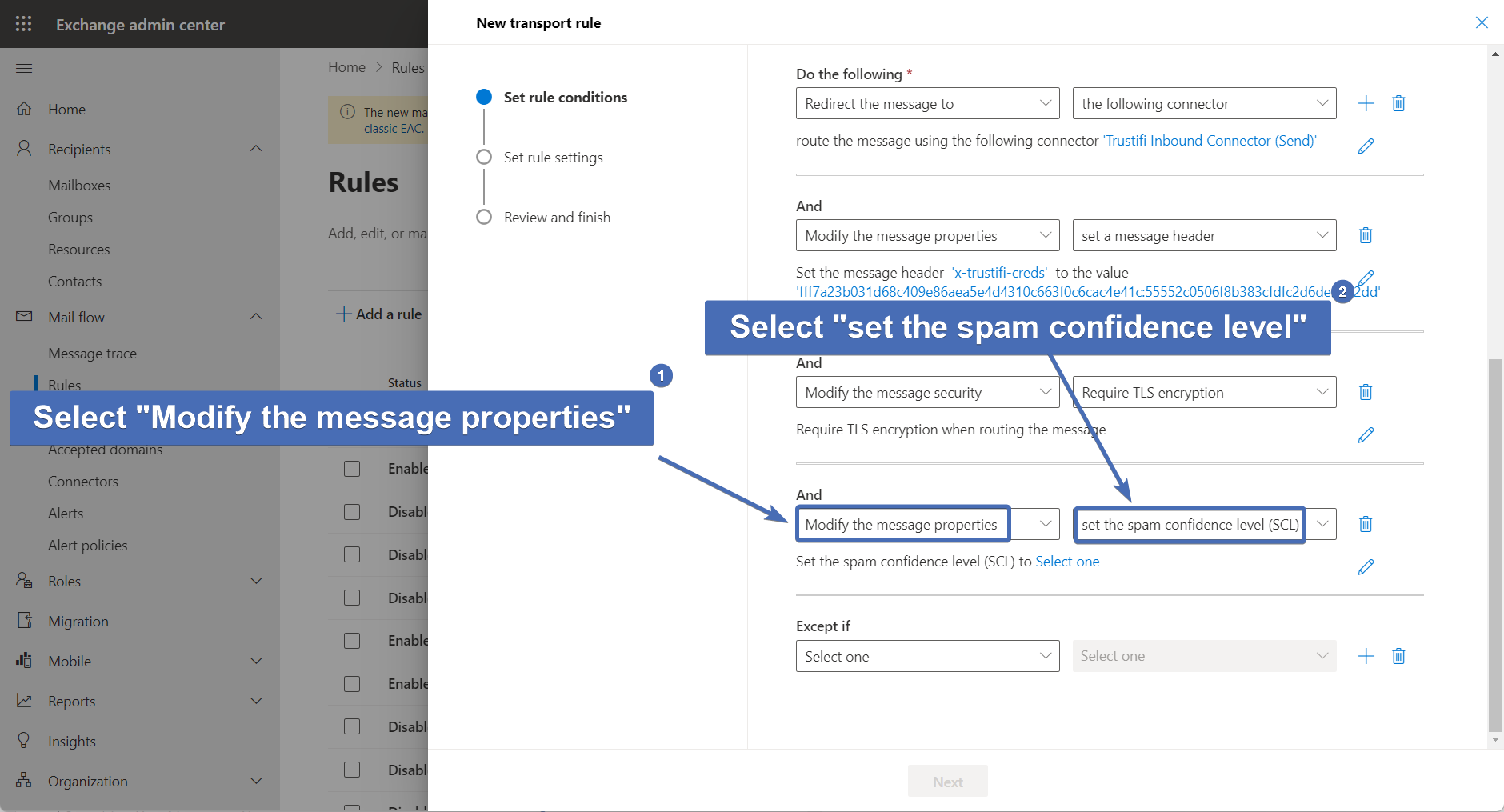
Step 48 – Fourth action: bypassing spam filtering
Add a new action for the rule. Then select "Modify the message properties" and "Set the spam confidence level (SCL)".
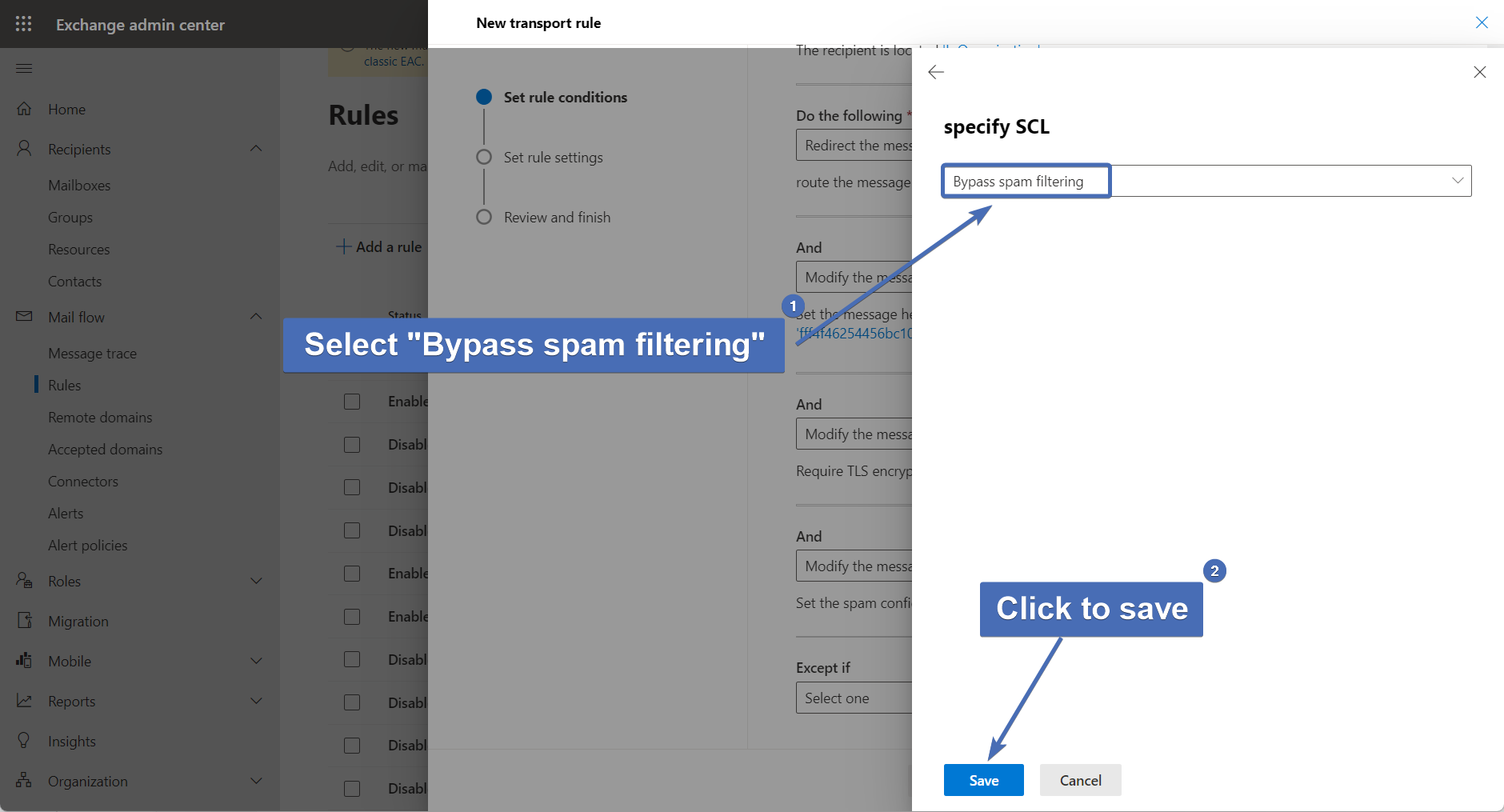
Step 49– Selecting spam bypass
In the "Specify SCL" window, select "Bypass spam filtering".
Then, click "Save".
Step 50 – Adding an exception: custom header
Here we will add a couple of exceptions to this mail flow rule to avoid processing emails which have already been sent by Trustifi. This is to avoid email loops. Under "Except if", select "The message headers" and then select "includes any of these words".
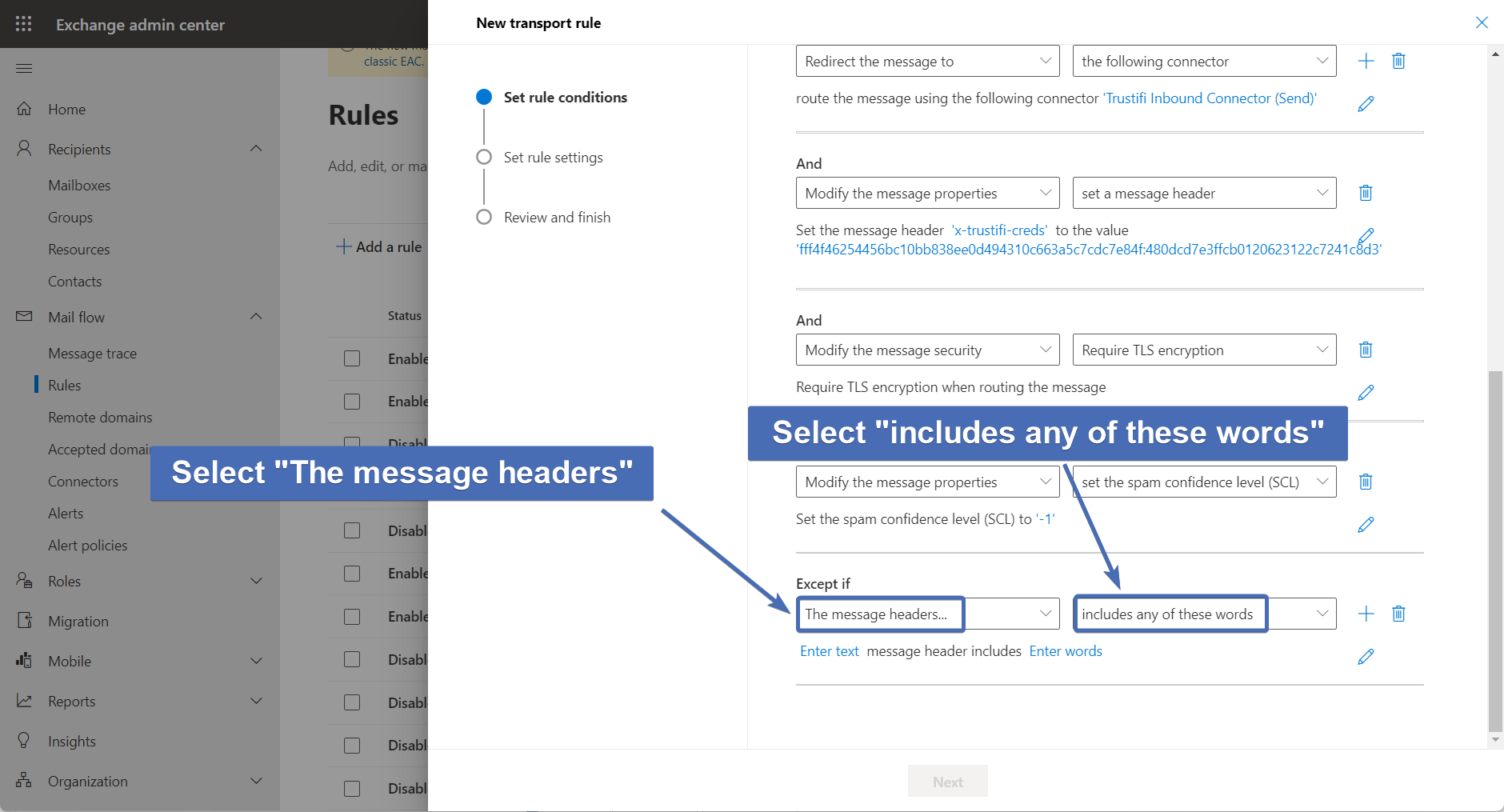 Step 51 – Setting the exception header name
Step 51 – Setting the exception header name
Click on the first “Enter text” link and in the pop-up window enter “x-trustifi-inbound-processed” (without the double quotes).
Click on “Save” to confirm.
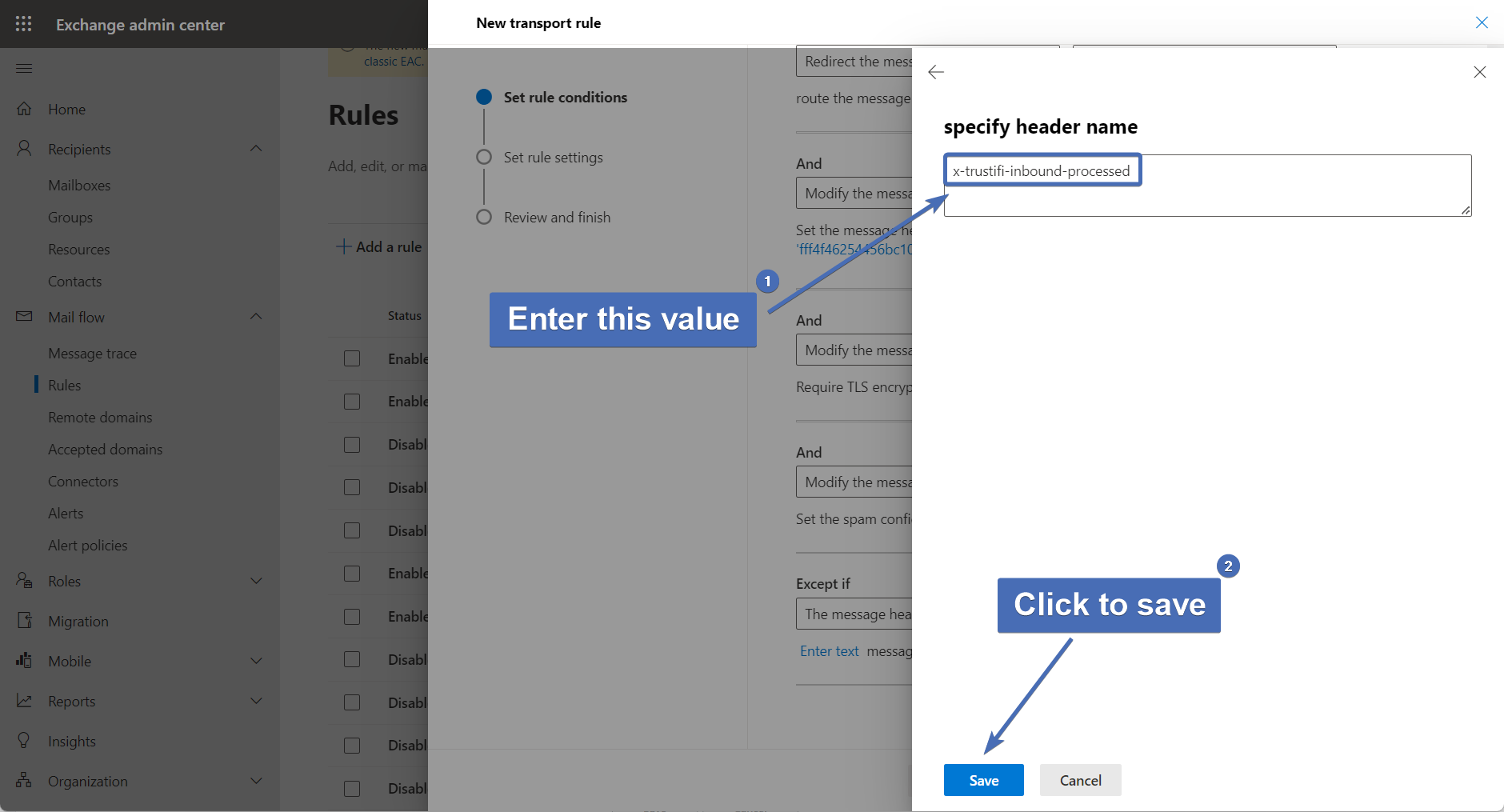
Step 52 – Setting the exception header value
Click on “Enter words” and in the pop-up window enter the word “yes” (without the double quotes).
Then click on the “+” icon and “Save” to confirm.
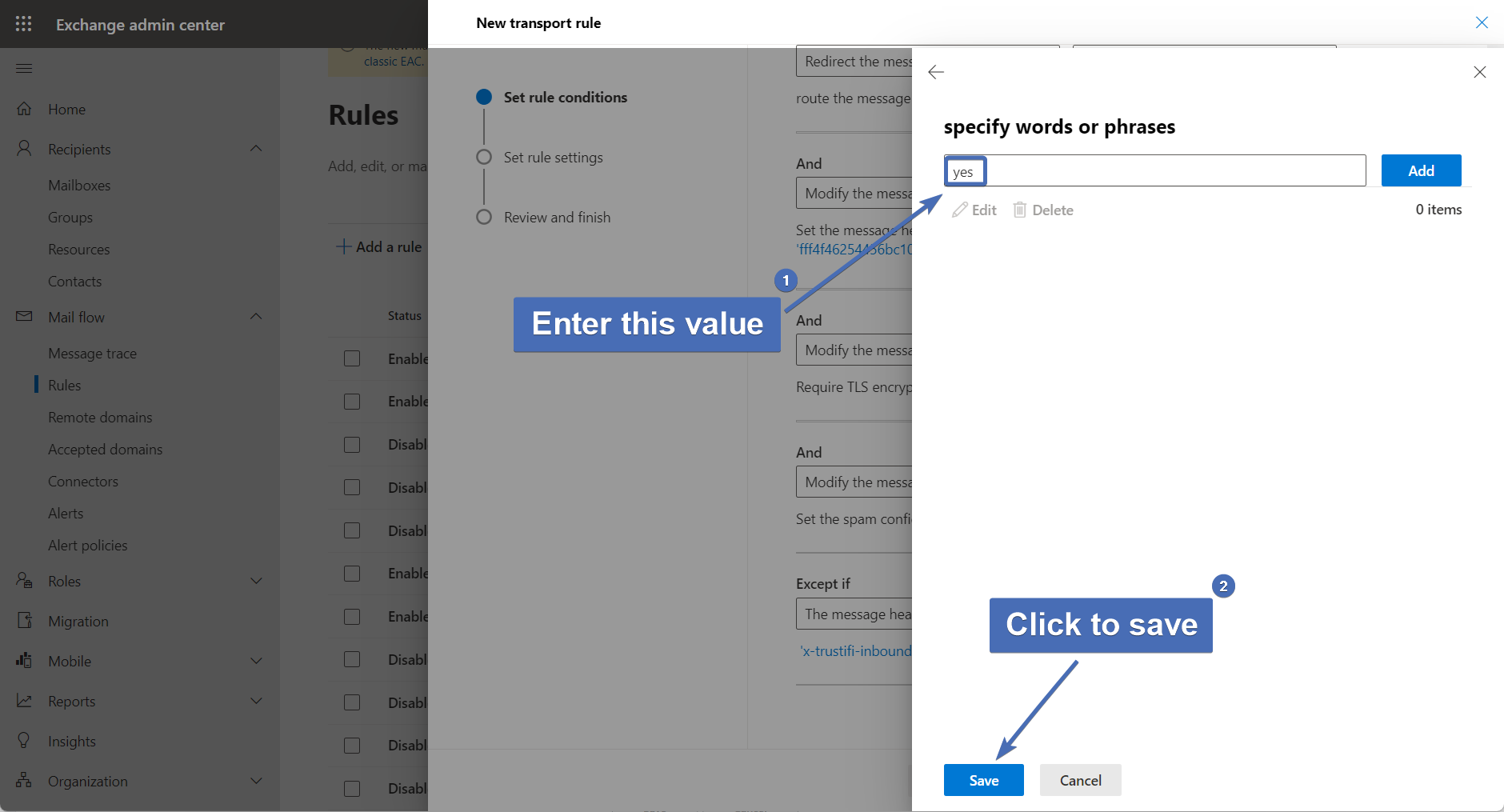
Step 53 – Creating the 2nd exception
Click on the "+" icon next to the first exception to add another exception.
Then select “The sender”, and “IP address is in any of these ranges or exactly matches”.
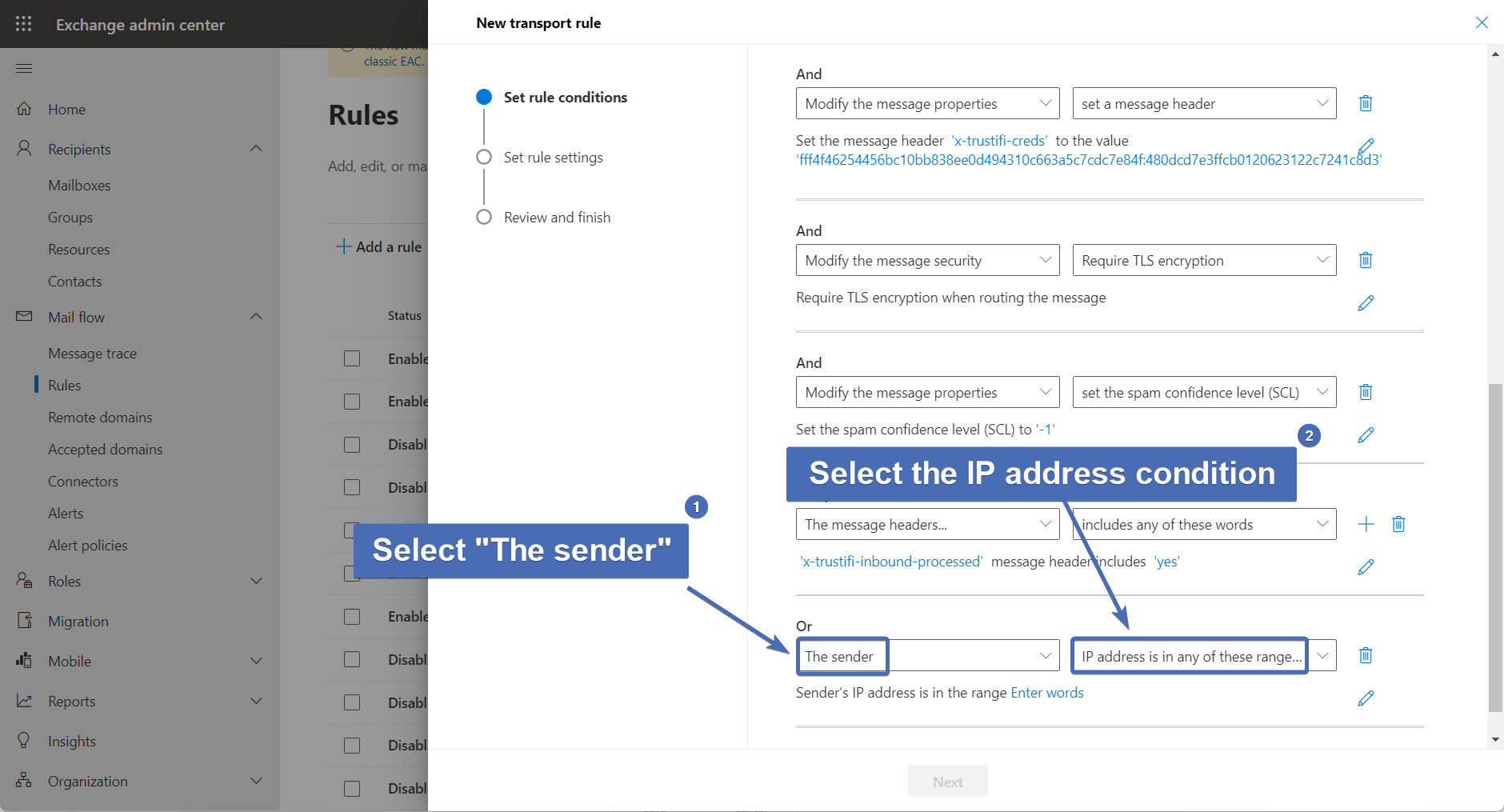
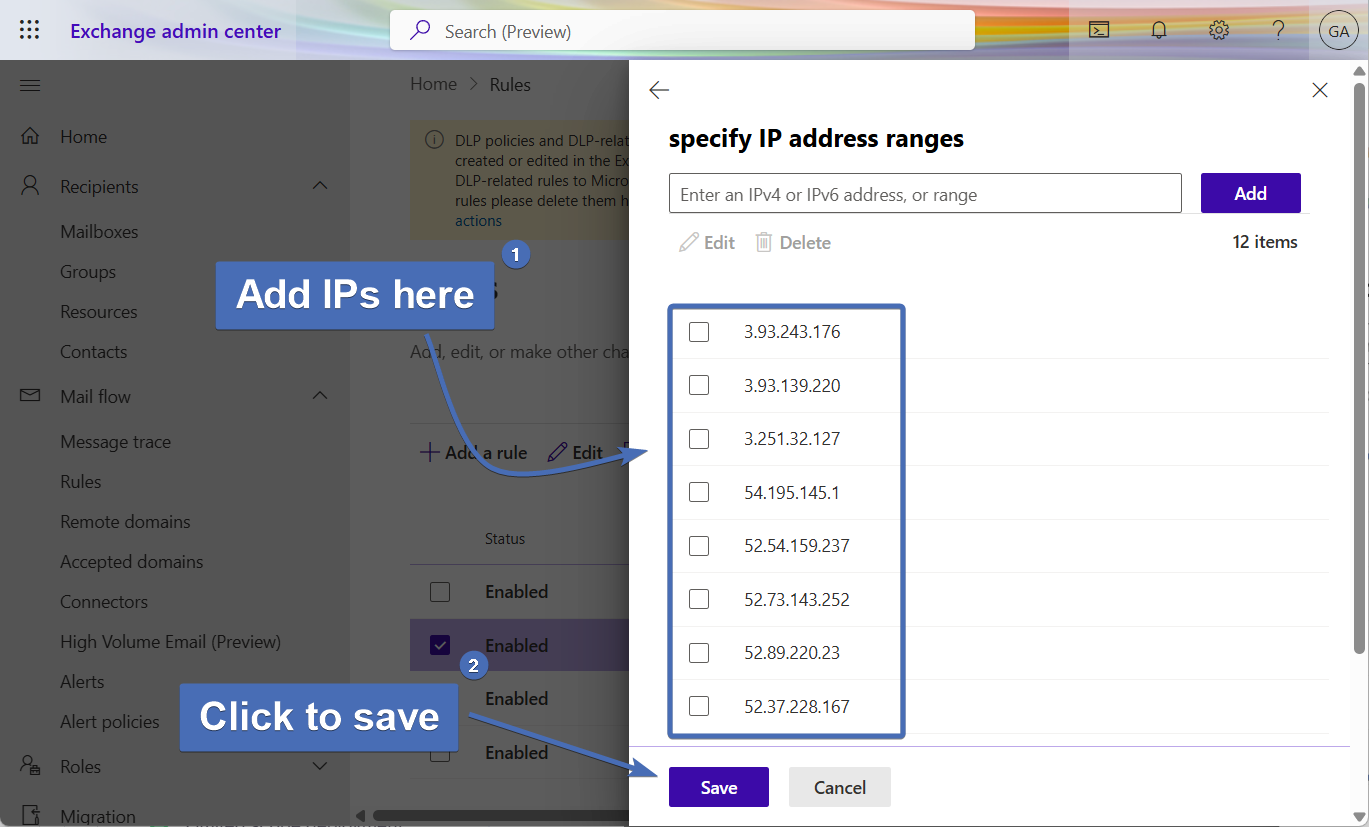
Step 54 – Adding the exception IPs
In the "specify IP address ranges" window, enter the following IPs:
3.93.243.176
3.93.139.220
3.251.32.127
54.195.145.1
52.89.220.23
52.37.228.167
52.54.159.237
52.73.143.252
3.221.25.19
34.192.117.166
44.209.231.3
35.172.145.174
Then, click on "Save".
Step 55 – Verifying the settings
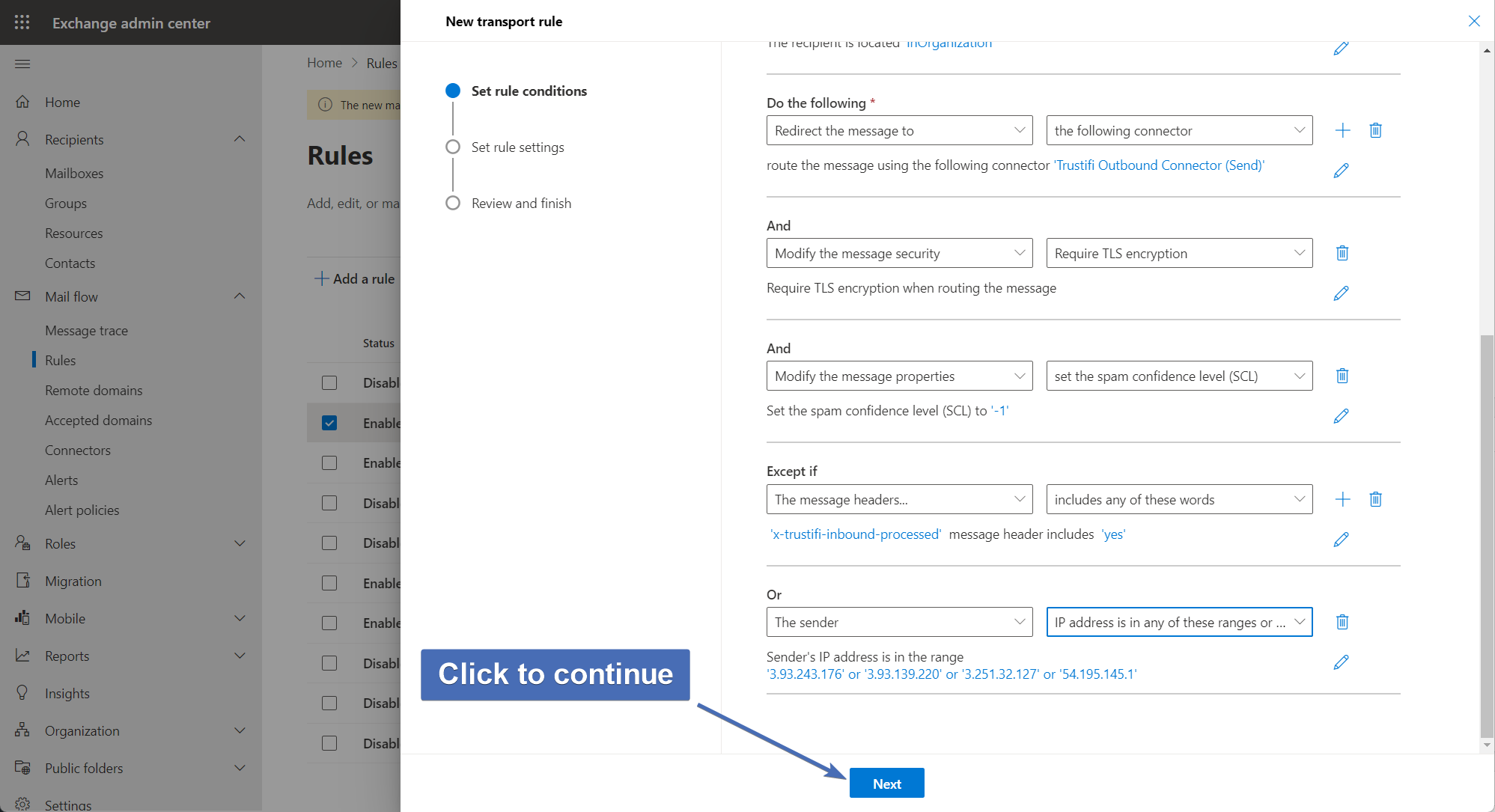
After both exceptions have been created, take a moment to verify all conditions, actions, and exceptions are correct.
If everything looks good, click on "Next".
 Step 56 – Rule settings
Step 56 – Rule settings
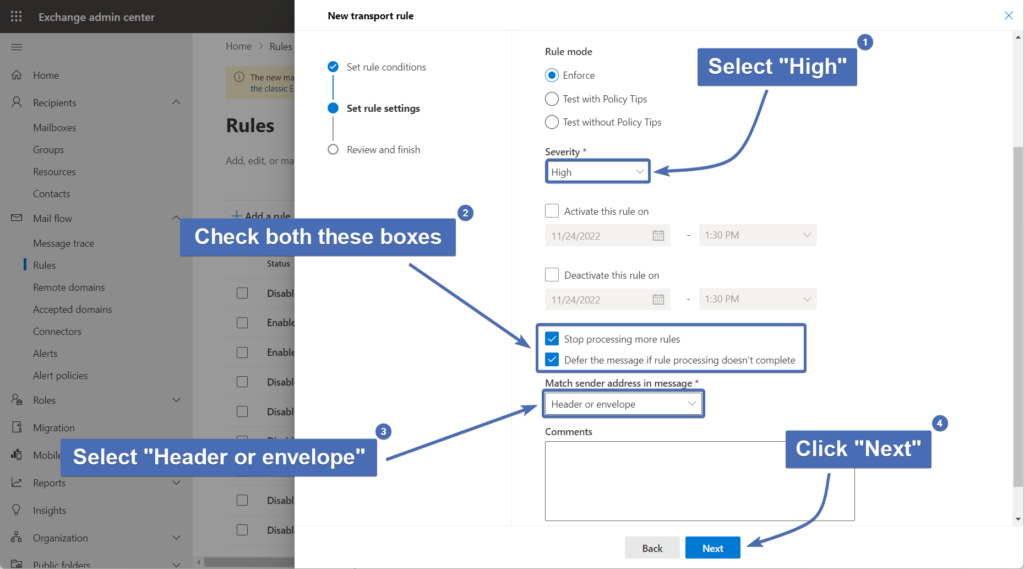
Set the following additional settings:
Under "Severity" - select "High"
Check the box for "Stop processing more rules"
Check the box for "Defer the message if rule processing doesn't complete
Under "Match sender address in message"- select "Header and envelope"
Once finished, click on "Next".
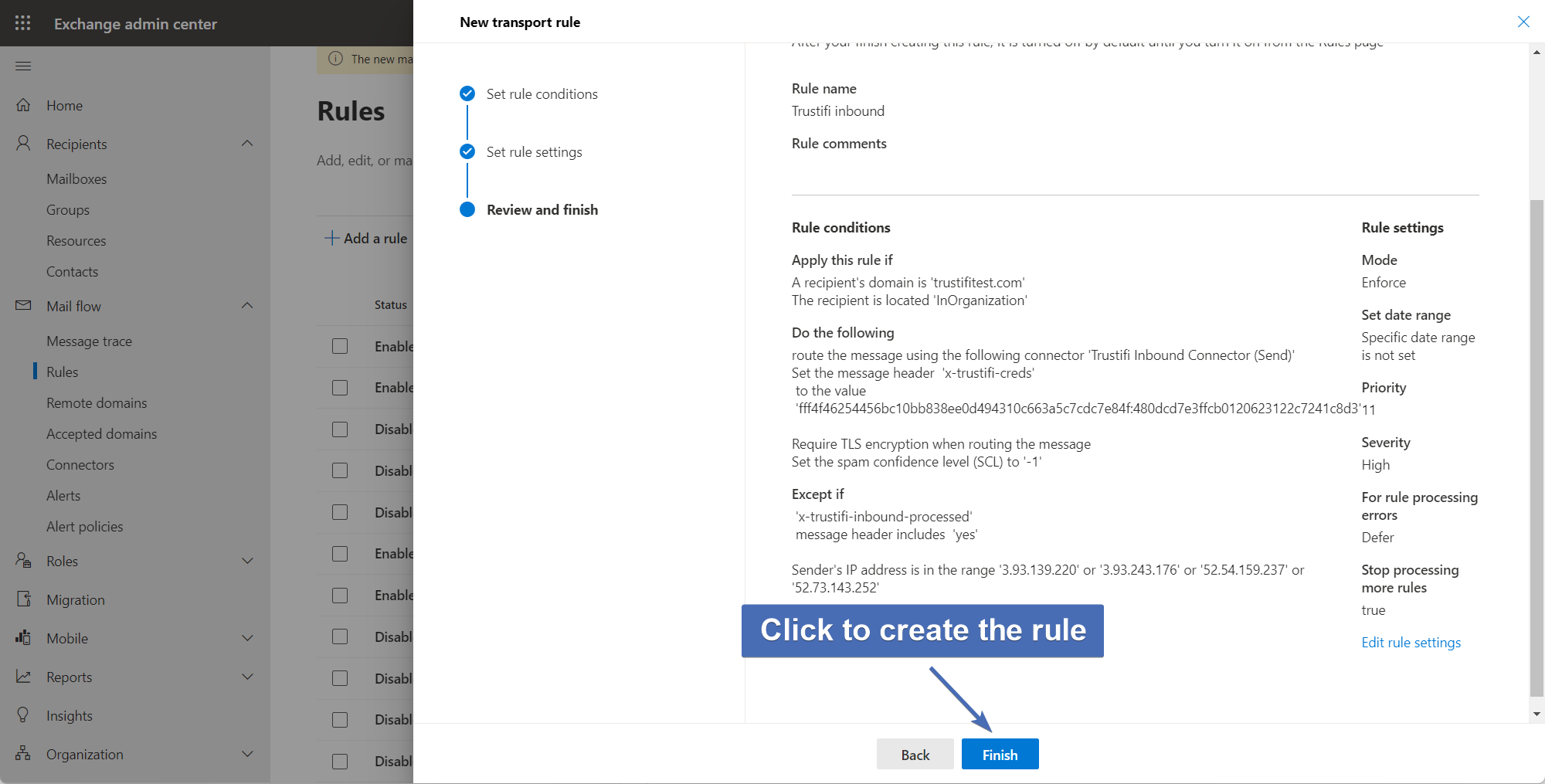
Step 57 – Review and finish
The next page will display a summary of the rule\'s conditions, actions, exceptions, and settings. Make sure that everything looks OK and click "Finish" to create the rule.
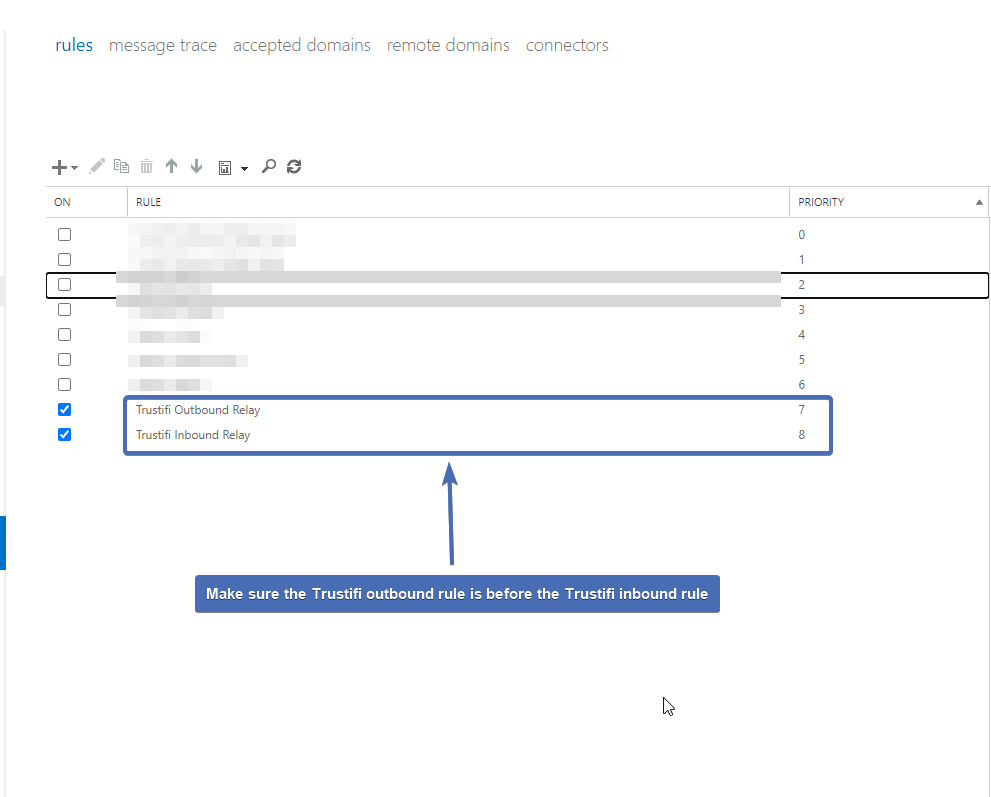
Step 58 – Verifying the rule priority order
If you are also connected to the Trustifi outbound relay, you will need to verify the 2 Trustifi mail flow rules are in the correct priority order.
To avoid issues with deliverability of internal emails, the Trustifi inbound mail flow rule has to come after the Trustifi outbound rule, as pictured below.